In right now’s cybersecurity panorama, evolving threats require safety options that match the sophistication of contemporary threats. As companies quickly undertake rising applied sciences, their publicity to cyberattacks will increase. To mitigate these dangers, cybersecurity groups want adaptable and complete instruments to guard their digital ecosystems successfully.
Safety Info and Occasion Administration (SIEM) and Prolonged Detection and Response (XDR) platforms play a serious function in lots of organizations’ cybersecurity methods.
These instruments present sturdy visibility, real-time monitoring, risk looking, and automatic response capabilities designed to handle rising cyber threats successfully.
The function of SIEM and XDR in fashionable safety
Safety Info and Occasion Administration (SIEM) and Prolonged Detection and Response (XDR) have develop into integral to complete safety methods. These applied sciences work collectively to supply real-time visibility, risk detection, and incident response throughout a corporation’s infrastructure, serving to to adequately shield in opposition to more and more subtle cyber threats.
SIEM options are an integral part of contemporary cybersecurity frameworks. They accumulate and analyze log information from varied sources, together with firewalls, servers, endpoints, and functions, to detect safety incidents and suspicious conduct.
By aggregating and analyzing log information, safety groups can establish patterns, anomalies, and potential threats, enabling them to handle vulnerabilities earlier than they disrupt operations.
XDR extends the capabilities of SIEM by delivering enhanced risk detection and response throughout a number of layers of a corporation’s IT infrastructure, together with endpoints, cloud environments, and networks. Whereas SIEM primarily focuses on log information and occasions, XDR integrates telemetry from various sources to supply a extra complete view of potential threats.
This integration permits XDR to detect superior threats and automate response actions, decreasing the handbook workload on safety groups.
SIEM and XDR kind a complete cyber protection mechanism that enhances risk visibility, improves response instances, and strengthens fashionable organizations’ total safety posture. Open supply SIEM and XDR platforms leverage community-driven innovation to repeatedly enhance their capacity to detect rising threats.
Advantages of leveraging open supply SIEM and XDR
Though many organizations have historically used proprietary safety options, open supply SIEM and XDR instruments have develop into more and more prevalent lately. Right here’s why:
- Price-effectiveness: Open supply SIEM and XDR instruments usually have diminished or no licensing charges, offering superior safety capabilities at decrease prices. This will make them appropriate for organizations with various budgets.
- Scalability: These instruments are designed to scale, permitting organizations to handle elevated workloads and monitor extra endpoints as their IT environments develop.
- Flexibility and customization: Open supply platforms permit for personalization, enabling organizations to adapt options and integrations to their particular safety necessities and infrastructure.
- Transparency: With entry to the supply code, open supply instruments allow organizations to conduct safety audits and confirm code integrity, supporting larger management over the software program’s reliability and compliance.
Wazuh is a free, open supply safety platform that gives SIEM and XDR capabilities for cloud and on-premises environments.
It affords complete capabilities, together with log information evaluation, file integrity monitoring, risk detection, real-time alerting, and automatic incident response, enabling efficient detection and response to evolving cybersecurity threats.
Listed below are some use circumstances the place Wazuh detects and responds to rising assaults:
Malware evasion methods
Malware stays one of the frequent threats attackers use to compromise techniques and steal delicate data. Wazuh gives protection in opposition to malware evasion by leveraging its out-of-the-box rulesets designed to detect and alert directors to any indicators of malicious actions.
Wazuh rulesets are pre-configured to observe varied indicators of compromise (IoCs) related to totally different malware variants. It permits customers to reinforce detection capabilities by creating customized guidelines and decoders to focus on particular actions or threats distinctive to their IT surroundings.
These customized configurations allow organizations to fine-tune the Wazuh functionality to detect extra specialised or focused assaults.
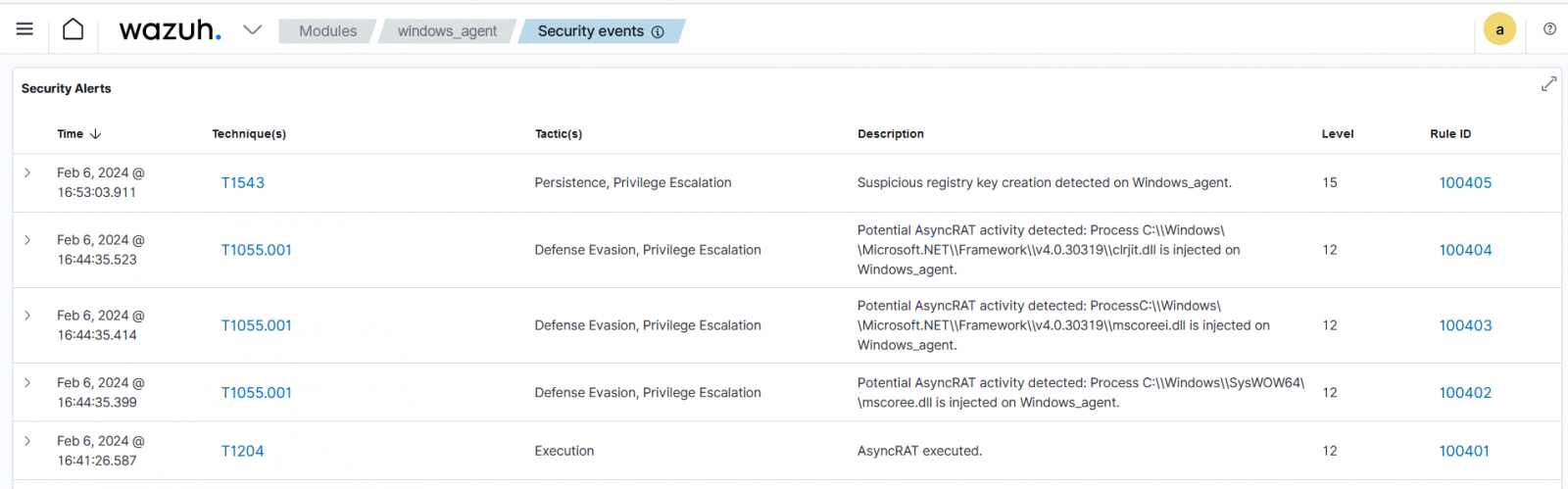
For instance, you’ll be able to configure Wazuh to detect AsyncRAT, an administrator distant entry instrument generally utilized by attackers to realize unauthorized management over compromised techniques.
The Wazuh agent gathers logs from the Home windows occasion channel and sends them to the Wazuh server for evaluation. The logs are filtered to detect AsyncRAT execution, associated system registry modifications, and different suspicious actions that point out the presence of this malware.
Ransomware assaults
Ransomware is a harmful and high-profile cyber risk. A profitable ransomware assault could cause devastating injury, usually resulting in important monetary losses and downtime.
Wazuh affords capabilities for detecting early indicators of ransomware assaults, enabling a fast response to reduce injury. Ransomware usually reveals a number of telltale indicators, similar to uncommon file entry patterns, encryption of enormous numbers of recordsdata, or communication with identified ransomware command and management (C2) servers.
Wazuh capabilities, similar to file integrity monitoring (FIM), run periodic scans on particular paths and monitor particular directories inside Wazuh brokers for modifications in real-time.
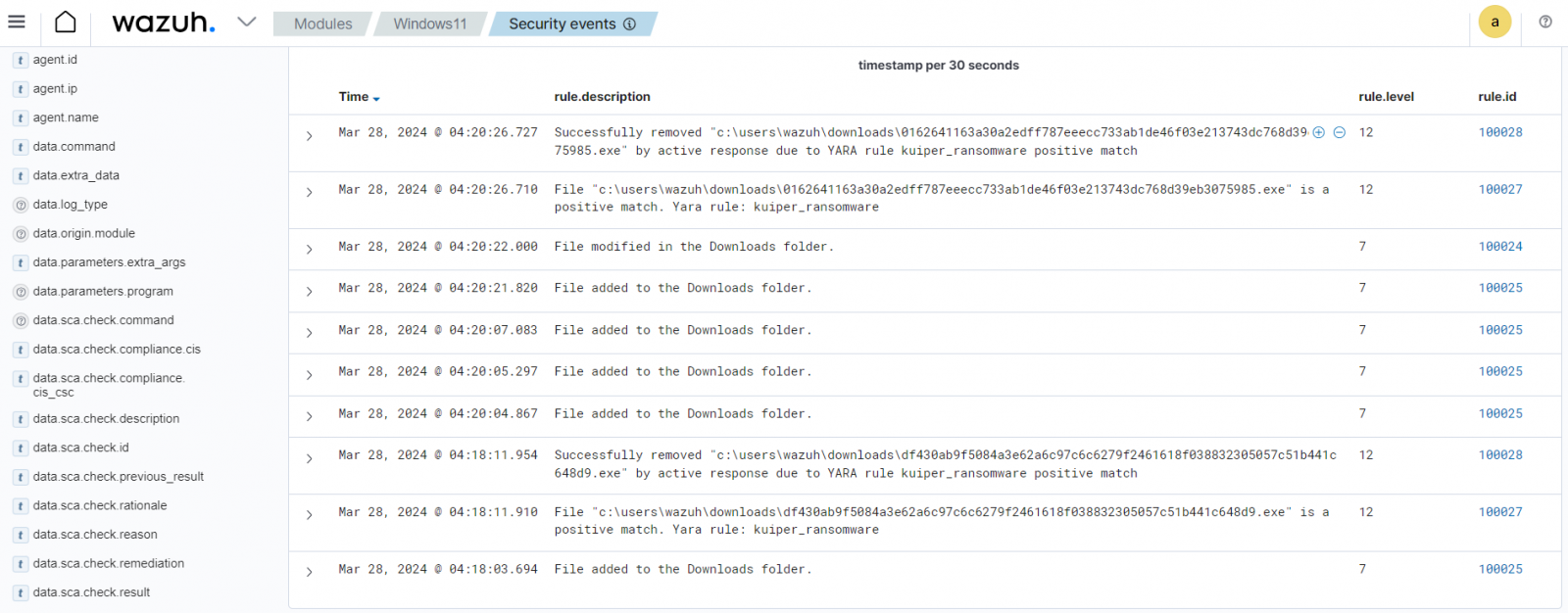
The weblog put up on Kuiper ransomware detection and response with Wazuh demonstrates how customers can mix Wazuh and YARA to safe monitored endpoints in opposition to ransomware.
By leveraging Wazuh File Integrity Monitoring functionality with YARA scan, customers obtain alerts when particular ransomware signatures are detected on monitored endpoints. This allows speedy identification and response to threats. An lively response script on the monitored endpoint triggers YARA scans to examine all added, modified, and deleted recordsdata for particular ransomware patterns.
If a malicious file is detected, the script mechanically makes an attempt to take away it.
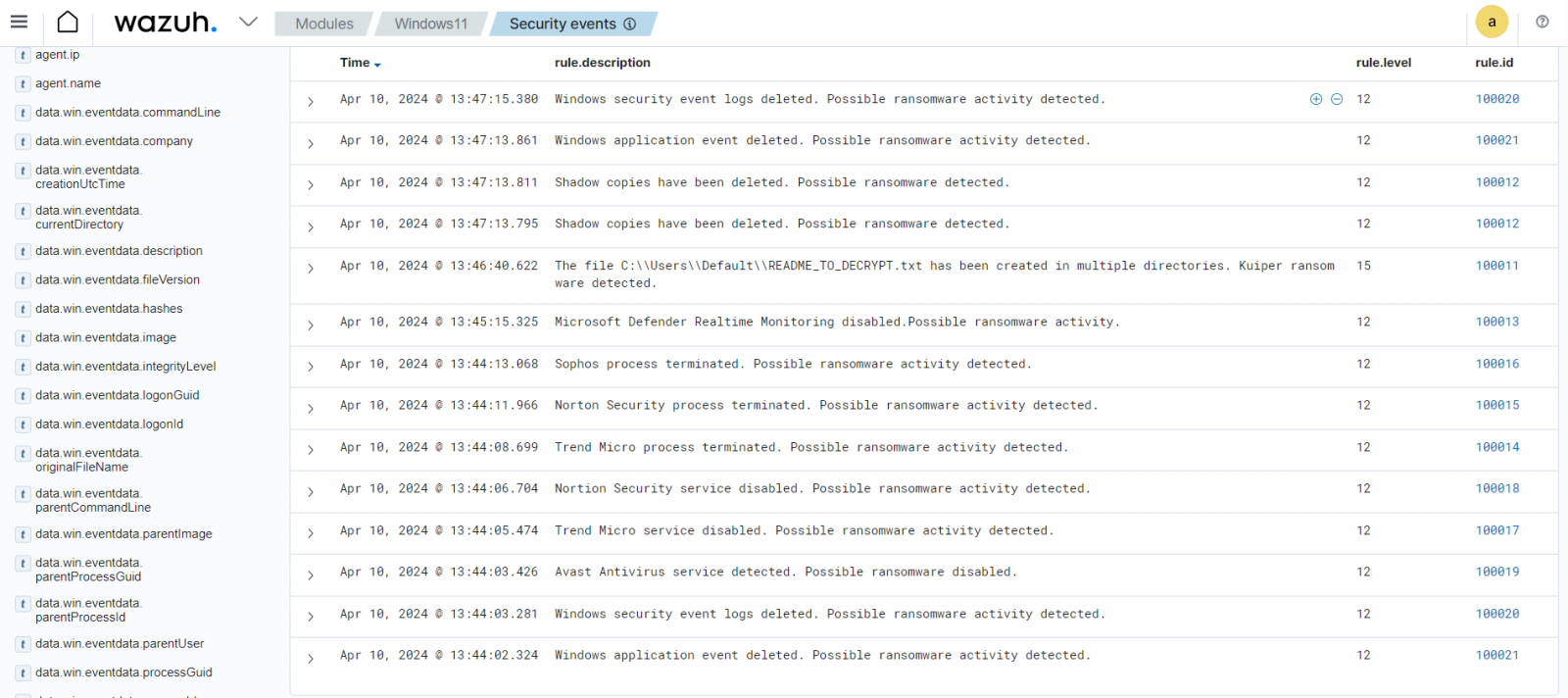
Ransomware assaults might be mechanically mitigated with the Wazuh lively response functionality.
Residing off the Land assaults
Residing off the Land (LOTL) assaults contain attackers utilizing reliable instruments on the sufferer’s endpoint to carry out malicious actions, making detection harder.
Frequent examples embrace using PowerShell, Home windows Administration Instrumentation (WMI), or different native system utilities to execute malicious instructions or scripts.
LOTL assaults usually evade conventional detection strategies as they usually keep away from deploying malware. Wazuh tackles this rising risk by monitoring system conduct and figuring out uncommon utilization of reliable instruments, enabling the detection of those refined actions.
Wazuh gives command monitoring functionality which monitors the output of particular executed instructions on monitored endpoints. Customers can configure Wazuh to seize and log particulars concerning the output of particular instructions, providing visibility into uncommon useful resource utilization by system processes.
Within the weblog put up monitoring Home windows sources with Efficiency Counters, customers can leverage Wazuh to trace system sources like CPU, RAM, disk, and community site visitors on monitored endpoints. Utilizing the Wazuh command monitoring functionality, you’ll be able to configure wodle instructions to run the Get-Counter cmdlet on the monitored endpoints and ship the output to the Wazuh server for evaluation.
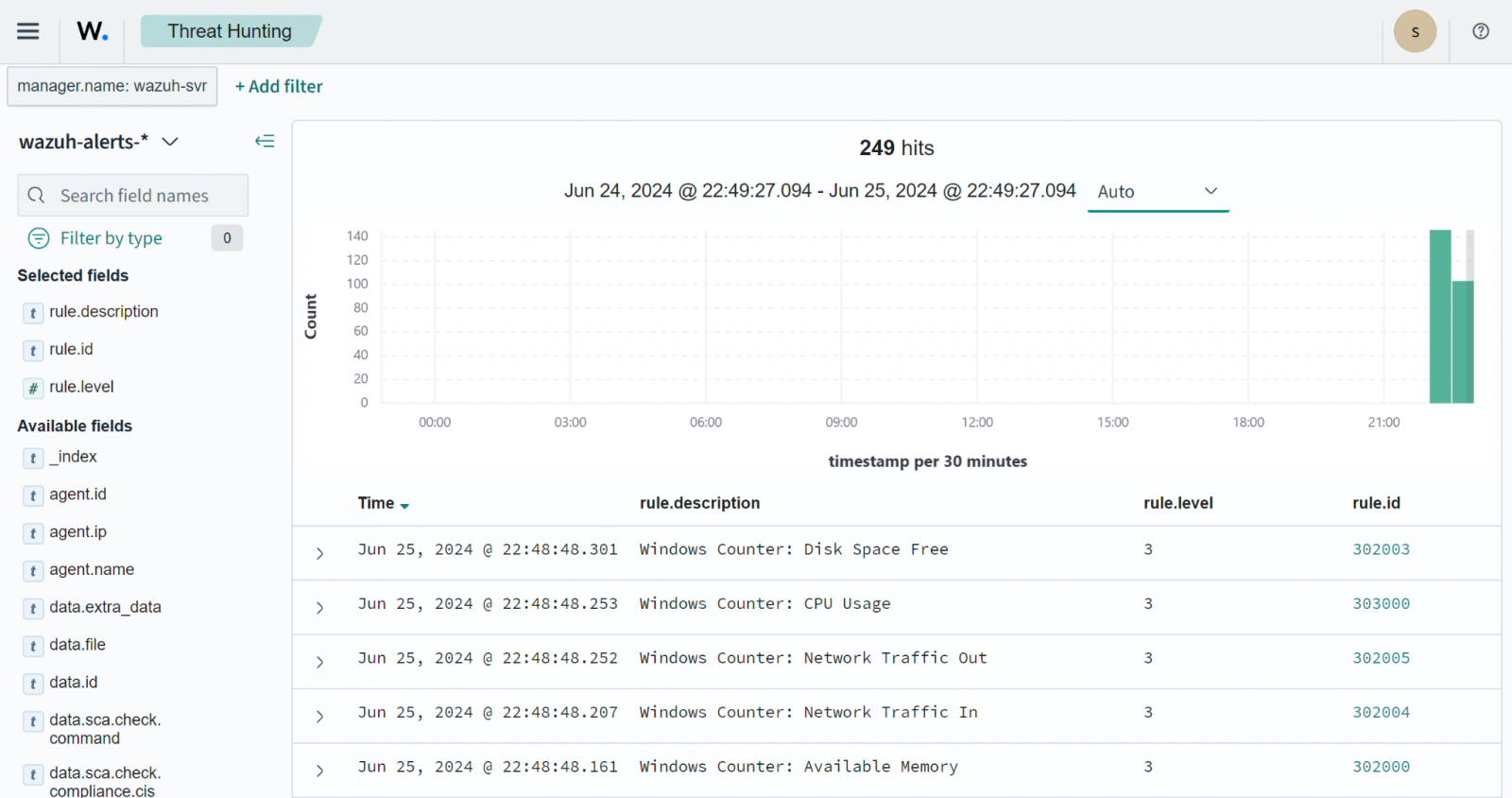
Vulnerability exploitation
Exploiting unpatched vulnerabilities stays a typical assault vector for cybercriminals, who goal outdated techniques or software program flaws to realize unauthorized entry. These vulnerabilities usually function the entry level for additional assaults, similar to distant code execution or malware set up.
Wazuh affords a vulnerability detection functionality that periodically scans working techniques and functions for vulnerabilities on monitored endpoints. It makes use of information from the Wazuh Cyber Menace Intelligence (CTI) platform, native repositories, and exterior sources like Canonical, Debian, Purple Hat, ALAS, Microsoft, and the Nationwide Vulnerability Database (NVD).
This allows the detection of outdated software program packages, with detailed vulnerability studies readily accessible on the Wazuh dashboard for simple monitoring and evaluation.
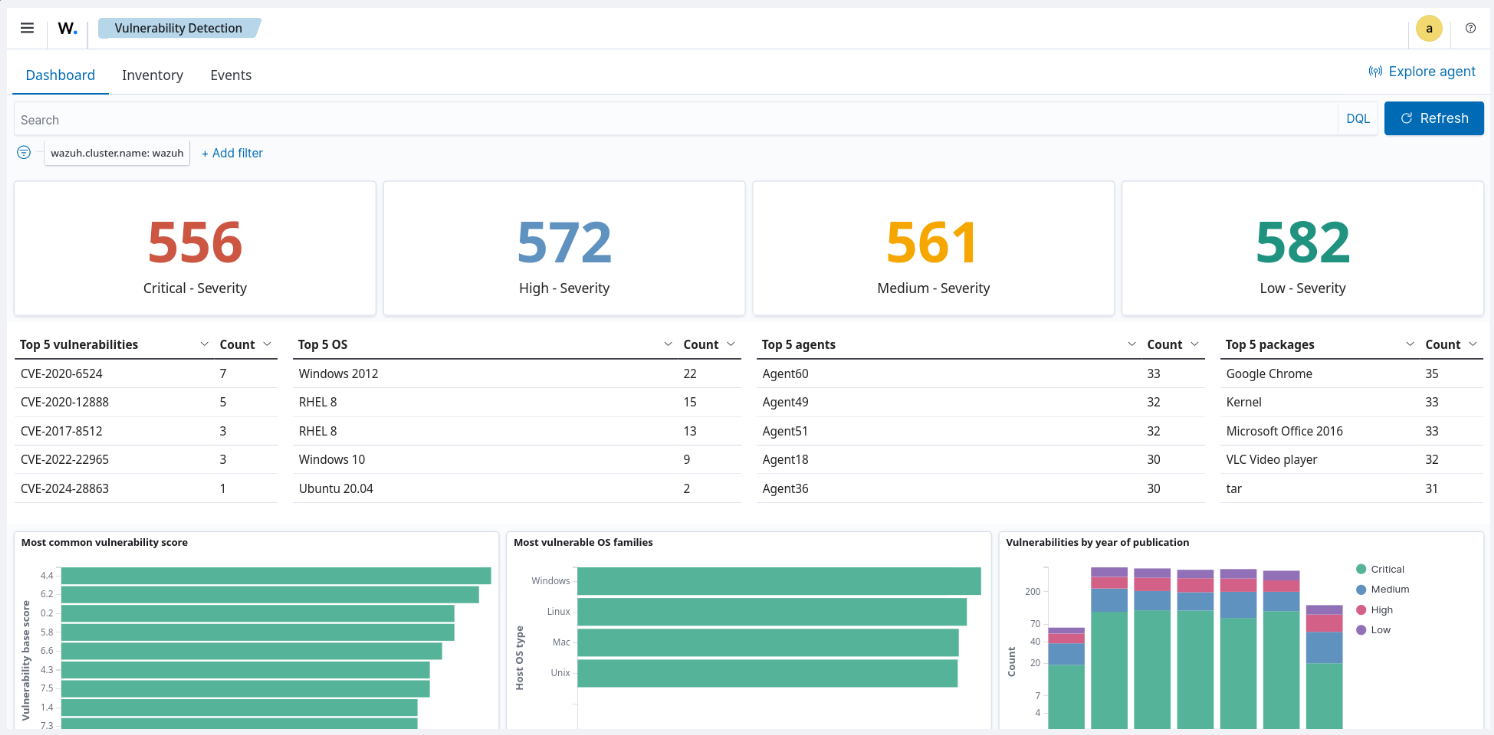
The weblog put up on detecting the XZ Utils vulnerability exploitation with Wazuh demonstrates how customers can establish potential exploitation of CVE-2024-3094 on their monitored endpoints. Customers can configure Wazuh brokers to detect and ship logs associated to suspicious sshd youngster processes to the Wazuh server for additional evaluation.
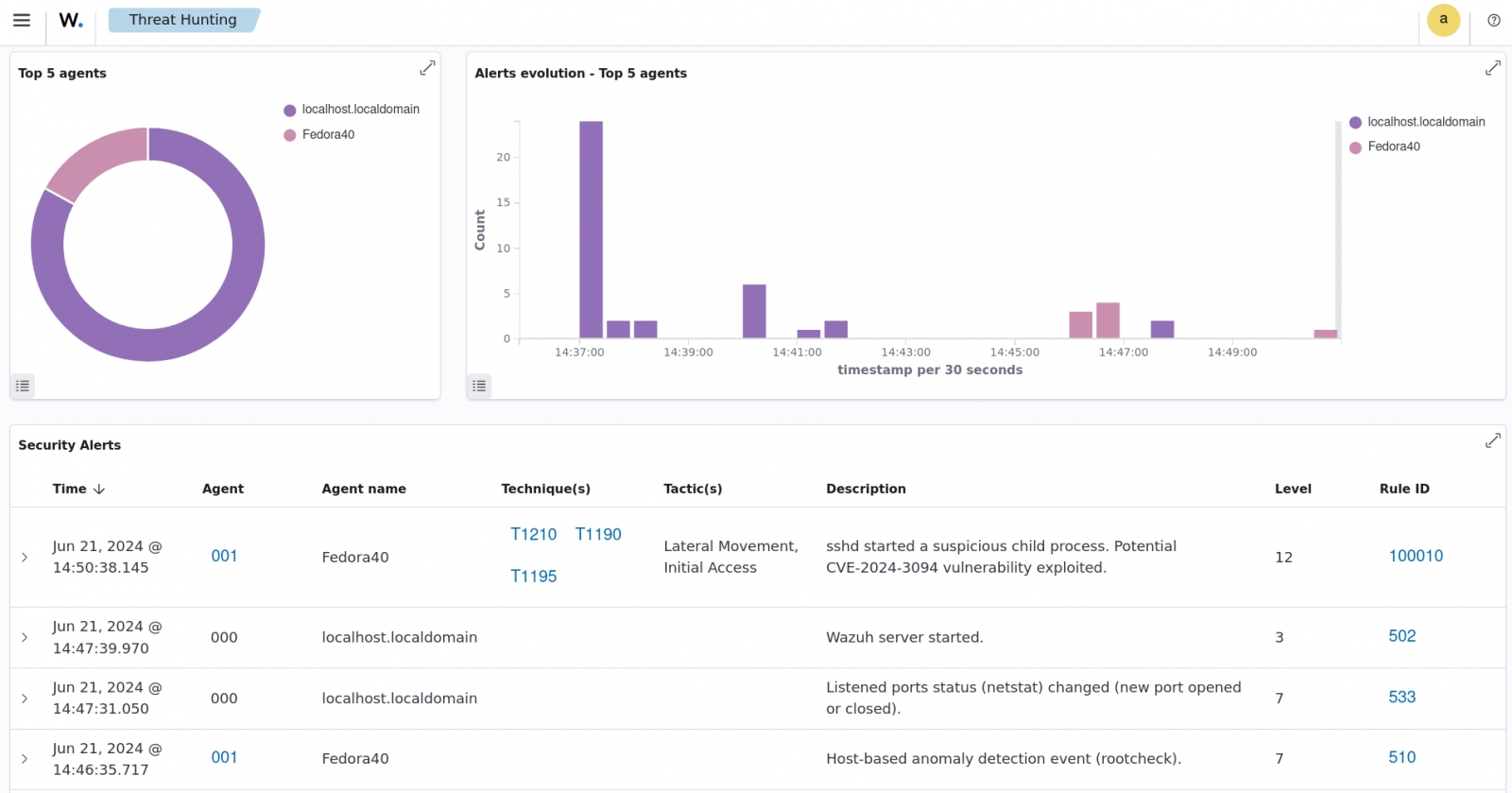
Conclusion
Using a strong safety strategy is important within the face of rising threats. Wazuh SIEM and XDR safety platform gives this with centralized visibility, automated responses, real-time insights into potential threats, and different capabilities.
By leveraging Wazuh, organizations might be higher ready to establish and mitigate threats. Wazuh additionally helps integration with third-party options to suit your particular use case and deal with the distinctive facets of your IT surroundings.
Uncover extra about Wazuh by exploring their documentation and becoming a member of their neighborhood for skilled assist.
Sponsored and written by Wazuh.