An APT hacking group often known as GoldenJackal has efficiently breached air-gapped authorities methods in Europe utilizing two customized toolsets to steal delicate information, like emails, encryption keys, photos, archives, and paperwork.
In keeping with an ESET report, this occurred a minimum of two occasions, one towards the embassy of a South Asian nation in Belarus in September 2019 and once more in July 2021, and one other towards a European authorities group between Might 2022 and March 2024.
In Might 2023, Kaspersky warned about GoldenJackal’s actions, noting that the risk actors concentrate on authorities and diplomatic entities for functions of espionage.
Though their use of customized instruments unfold over USB pen drives, just like the ‘JackalWorm,’ was identified, circumstances of a profitable compromise of air-gapped methods weren’t beforehand confirmed.
Air-gapped methods are utilized in important operations, which regularly handle confidential data, and are remoted from open networks as a safety measure.
Coming into by the (air)hole
The older assaults seen by ESET start by infecting internet-connected methods, possible utilizing trojanized software program or malicious paperwork, with a malware known as ‘GoldenDealer.’
GoldenDealer displays for the insertion of USB drives on these methods, and when it occurs, it robotically copies itself and different malicious parts onto it.
Ultimately, that very same USB drive is inserted into an air-gapped pc, permitting GoldenDealer to put in GoldenHowl (a backdoor) and GoldenRobo (a file stealer) onto these remoted methods.
Throughout this part, GoldenRobo scans the system for paperwork, photos, certificates, encryption keys, archives, OpenVPN configuration information, and different invaluable information and shops them in a hidden listing on the USB drive.
When the USB drive is faraway from the air-gapped pc and re-connected to the unique internet-connected system, GoldenDealer robotically sends the stolen information saved on the drive to the risk actor’s command and management (C2) server.
GoldenHowl is a multi-functional Python backdoor that may steal information, facilitate persistence, scan for vulnerabilities, and talk immediately with the C2. ESET says it seems designed to run on internet-connected machines.
.jpg)
Supply: ESET
New modular toolset
In 2022, GoldenJackal started utilizing a brand new Go-based modular toolset that carried out related actions to these described within the earlier part however allowed the attackers to job totally different machines with separate roles.
For instance, some machines have been used for file exfiltration whereas others acted as file stagers or configuration distribution factors.
The brand new malware used for USB an infection is known as GoldenAce, and the instruments that steal information and ship them to the attackers are named ‘GoldenUsbCopy’ and ‘GoldenUsbGo,’ with the latter being a more moderen variant of the previous.
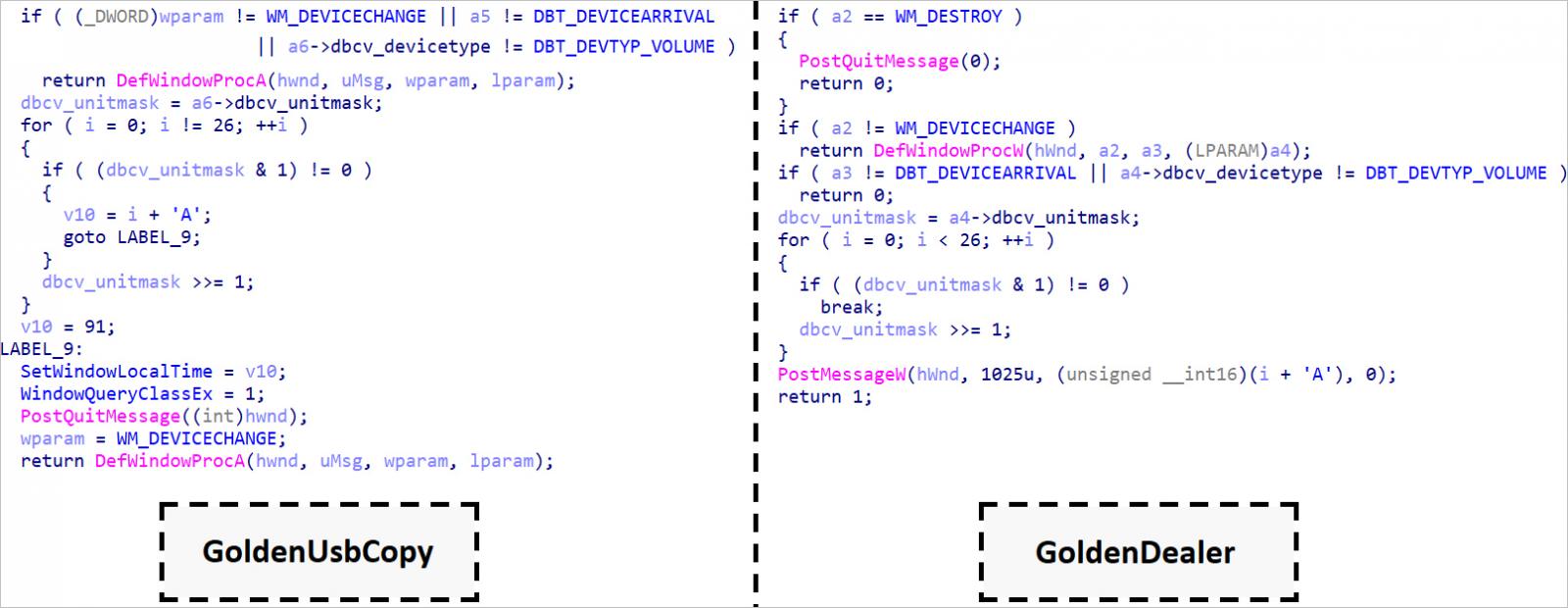
Supply: ESET
GoldenUsbGo now not makes use of AES-encrypted configuration however as an alternative exfiltrates information based mostly on hardcoded directions, together with not too long ago (as much as 14 days) modified information which might be smaller than 20 MB and match particular kinds of content material (key phrases like “pass”, “login”, or “key”) or sure file varieties (.pdf, .doc/.docx, .sh, .bat).
One other attention-grabbing malware element is GoldenBlacklist (and its Python-based implementation GoldenPyBlacklist), which filters and archives particular electronic mail messages from compromised methods earlier than exfiltration.
Lastly, there’s GoldenMailer, which emails the stolen data to the attackers, and GoldenDrive, which uploads the information to Google Drive.
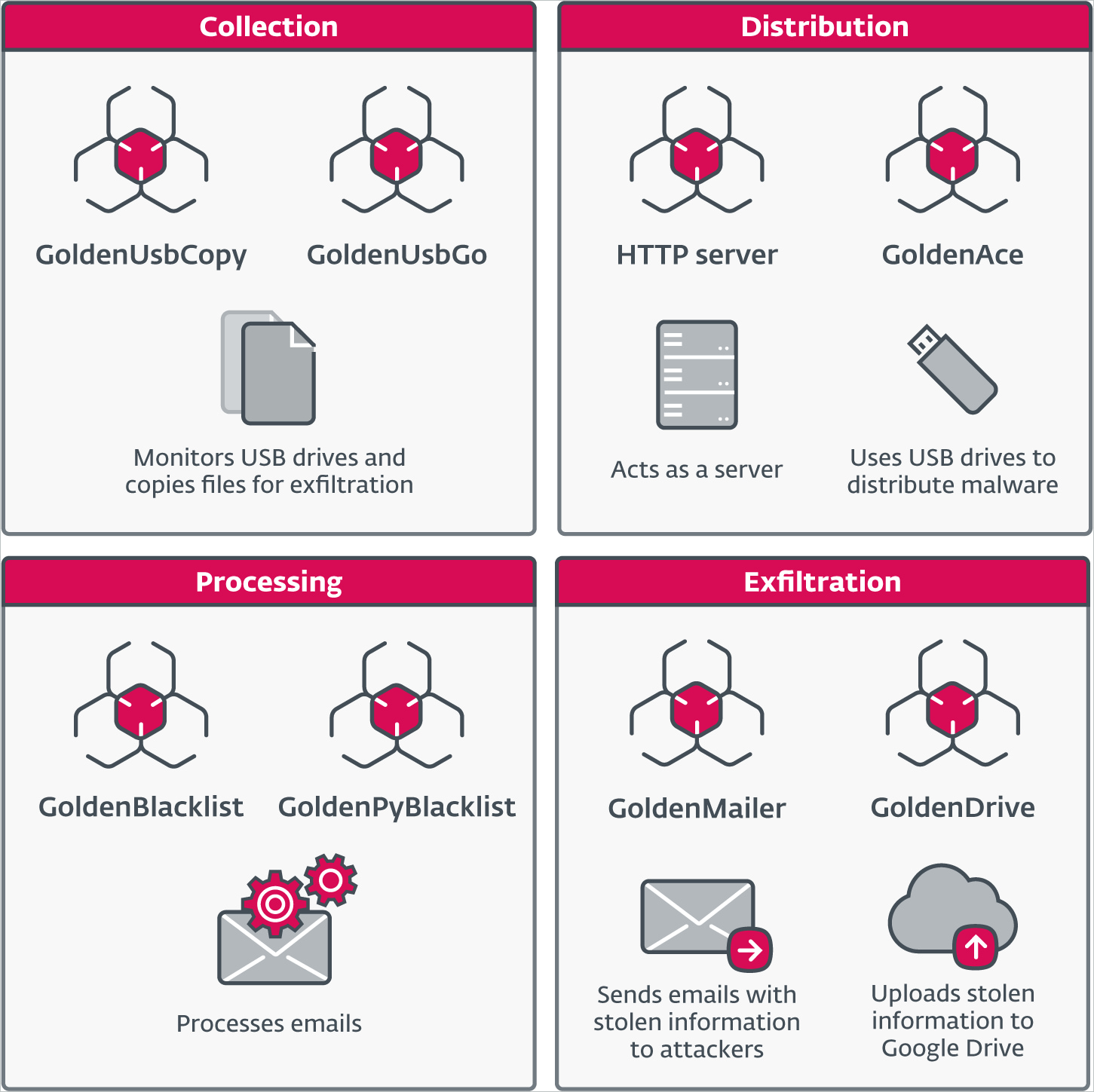
Supply: ESET
The presence of two toolsets that additionally overlap with instruments described in Kaspersky’s report demonstrates GoldenJackal’s functionality to develop new customized malware and optimize it for covert espionage operations.
For an entire record of the indications of compromise (IoCs) related to all these instruments, you possibly can try this GitHub web page.
