An automatic scanner has been launched to assist safety professionals scan environments for units weak to the Widespread Unix Printing System (CUPS) RCE flaw tracked as CVE-2024-47176.
The flaw, which allows attackers to carry out arbitrary distant code execution if sure circumstances are met, was disclosed late final month by the one who found it, Simone Margaritelli.
Though its RCE facet seems restricted in real-world deployments because of the stipulations for exploitation, Akamai later confirmed that CVE-2024-47176 additionally opened the likelihood for 600x amplification in distributed denial of service (DDoS) assaults.
The scanner was created by cybersecurity researcher Marcus Hitchins (aka “MalwareTech”), who created the scanner to assist system directors scan their networks and rapidly establish units working weak CUPS-Browsed companies.
“The vulnerability arises from the fact that cups-browsed binds its control port (UDP port 631) to INADDR_ANY, exposing it to the world. Since requests are not authenticated, anyone capable of reaching the control port can instruct cups-browsed to perform printer discovered.”
“In cases when the port is not reachable from the internet (due to firewalls or NAT), it may still be reachable via the local network, enabling privilege escalation and lateral movement.”
“For this reason, I’ve created this scanner designed to scan your local network for vulnerable cups-browsed instances.” – Marcus Hitchins
How the scanner works
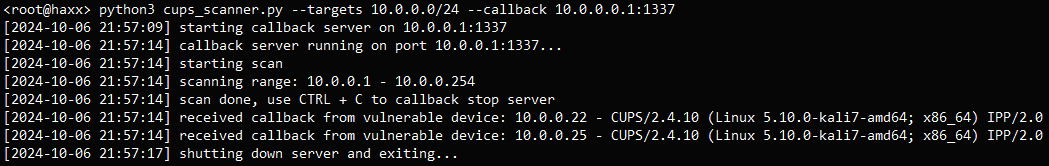
The Python script (cups_scanner.py) units up an HTTP server on the scanning machine that listens for incoming HTTP requests (callbacks) from units on the community.
CVE-2024-47176 arises from CUPS-browsed (a daemon a part of CUPS) binding its management port (UDP port 631) to INADDR_ANY, exposing the port to the community and permitting any system to ship instructions to it.
The scanner sends a customized UDP packet to the community’s broadcast handle on port 631, despatched to every IP handle within the specified vary, telling CUPS situations to ship a request again.
If a tool working a weak cups-browsed occasion receives the UDP packet, it’ll interpret the request and ship an HTTP callback to the server, so solely people who reply are marked as weak.
Supply: GitHub
The outcomes are written in two logs: one (cups.log) containing the IP addresses and CUPS model of the units that responded and one (requests.log) containing the uncooked HTTP requests obtained by the callback server that can be utilized for deeper evaluation.
Through the use of this scanner, system directors can plan and execute focused patching or reconfiguration motion, minimizing the publicity of CVE-2024-47176 on-line.
BleepingComputer has not examined the script and can’t guarantee its effectiveness or security, so you need to use it at your personal threat.
