An rising phishing-as-a-service (PhaaS) platform known as Mamba 2FA has been noticed concentrating on Microsoft 365 accounts in AiTM assaults utilizing well-crafted login pages.
Moreover, Mamba 2FA gives menace actors an adversary-in-the-middle (AiTM) mechanism to seize the sufferer’s authentication tokens and bypass multi-factor authentication (MFA) protections on their accounts.
Mamba 2FA is at present offered to cybercriminals for $250/month, which is a aggressive value that positions it among the many most alluring and fastest-growing phishing platforms within the house.
Discovery and evolution
Mamba 2FA was first documented by Any.Run analysts in late June 2024, however Sekoia studies that it has been monitoring exercise linked to the phishing platform since Might 2024.
Further proof exhibits that Mamba 2FA has been supporting phishing campaigns since November 2023, with the equipment being offered on ICQ and in a while Telegram.
Following Any.Run’s report of a marketing campaign backed by Mamba 2FA, the operators of the phishing equipment made a number of modifications to their infrastructure and strategies to extend the stealthiness and longevity of the phishing campaigns.
For instance, beginning in October, Mamba 2FA launched proxy servers sourced from IPRoyal, a business supplier, to masks the IP addresses of relay servers on authentication logs.
Beforehand, relay servers related on to Microsoft Entra ID servers, exposing the IP addresses and making blocks simpler.
Hyperlink domains utilized in phishing URLs are actually very short-lived and usually rotated weekly to keep away from blocklisting by safety options.
One other change was enhancing HTML attachments utilized in phishing campaigns with benign filler content material to cover a small snippet of JavaScript that triggers the assault, making it tougher for safety instruments to detect.
“Biting” Microsoft 365 customers
Mamba 2FA is particularly designed to focus on customers of Microsoft 365 providers, together with company and shopper accounts.
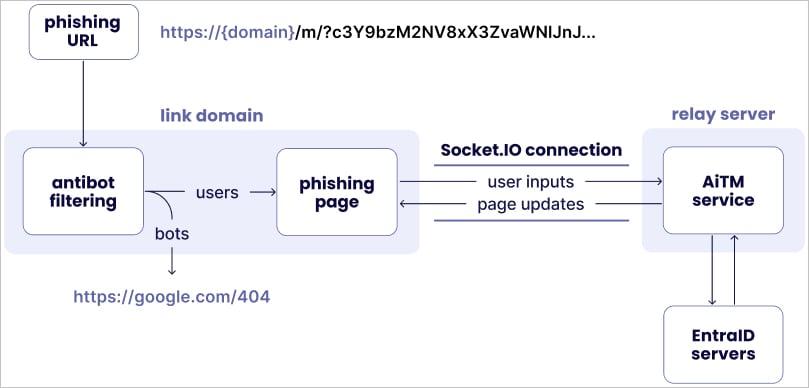
Like different comparable PhaaS platforms, it makes use of proxy relays to conduct AiTM phishing assaults, permitting the menace actors to entry one-time passcodes and authentication cookies.
The AiTM mechanism makes use of the Socket.IO JavaScript library to determine communication between the phishing web page and the relay servers on the backend, which in flip talk with Microsoft’s servers utilizing the stolen information.
Supply: Sekoia
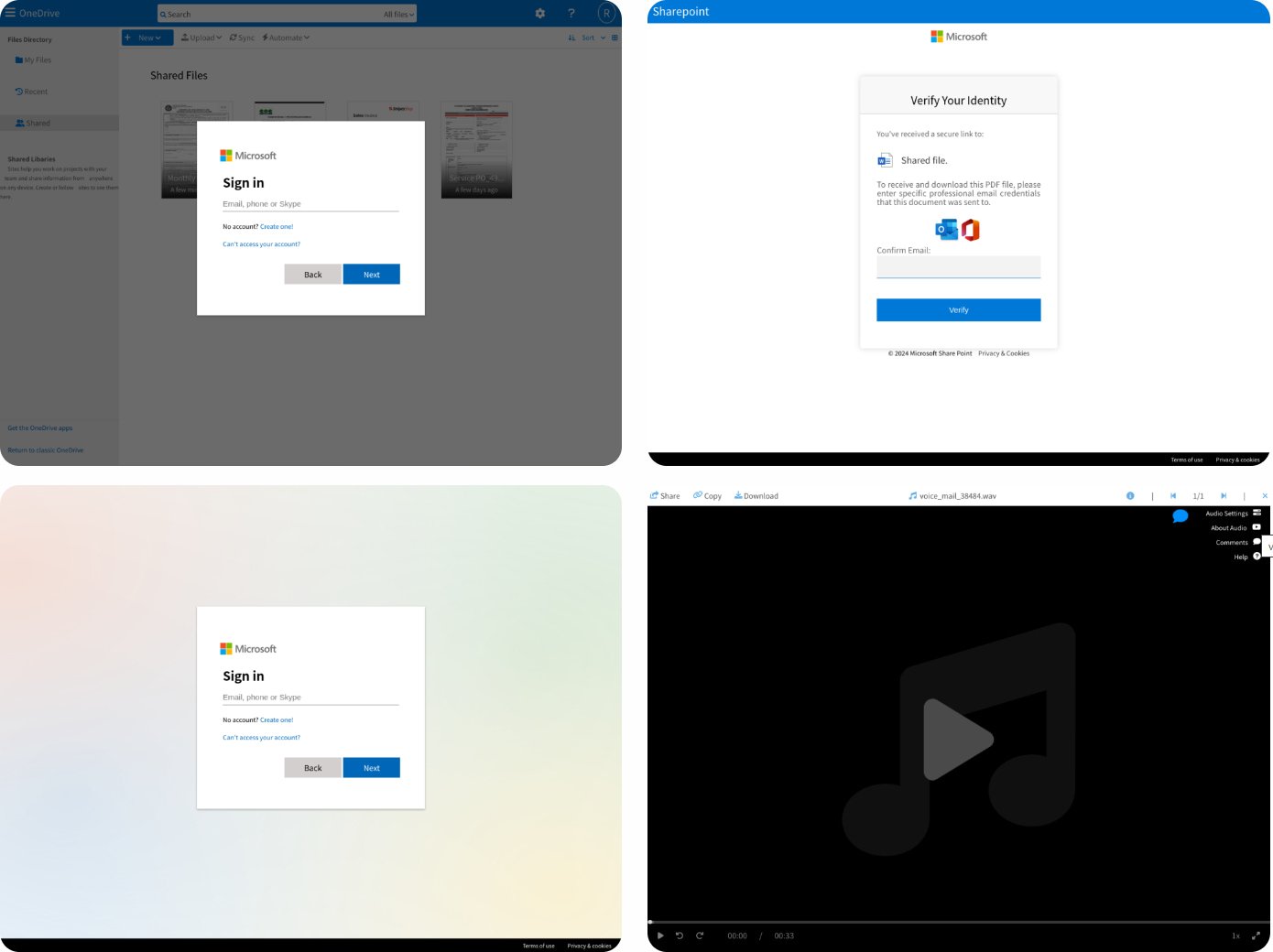
Mamba 2FA gives phishing templates for varied Microsoft 365 providers, together with OneDrive, SharePoint On-line, generic Microsoft sign-in pages, and pretend voicemail notifications that redirect to a Microsoft login web page.
For enterprise accounts, the phishing pages dynamically assume the focused group’s customized login branding, together with logos and background photos, making the try seem extra genuine.
Supply: Sekoia
Captured credentials and authentication cookies are transmitted to the attacker by means of a Telegram bot, enabling them to provoke a session instantly.
Mamba 2FA additionally options sandbox detection, redirecting customers to Google 404 webpages when it deduces it is being beneath evaluation.
General, the Mamba 2FA platform is yet one more menace to organizations, permitting low-skilled actors to carry out extremely efficient phishing assaults.
To guard towards PhaaS operations utilizing AiTM ways, think about using {hardware} safety keys, certificate-based authentication, geo-blocking, IP allowlisting, gadget allowlisting, and token lifespan shortening.
