DevSecOps: The place Are We Now?
DevOps represents the basic cultural shift in software program engineering in the direction of efficiency: excessive performing groups, and excessive efficiency code.
In DevOps, safety was by no means a major consideration.
DevSecOps represents the truth that DevOps should develop to embody safety. Ultimately, performant code will imply safe code by default – however we’re not there but. How will we get there?
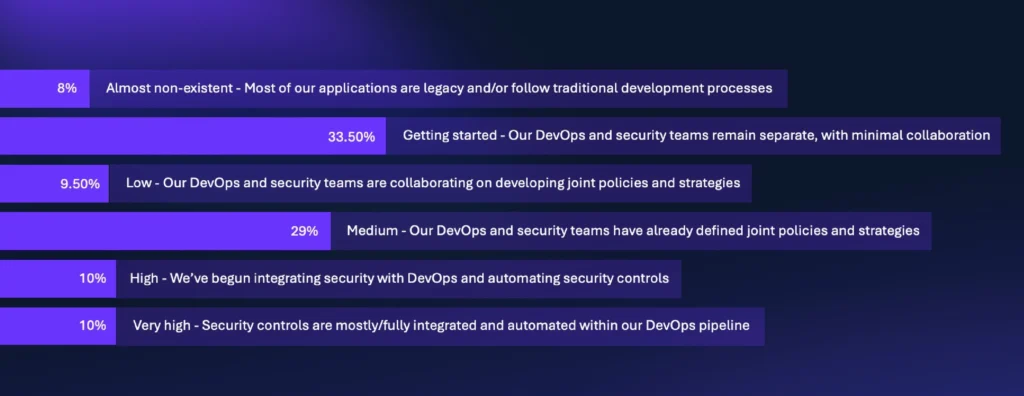
Let’s begin with the place we are actually. Earlier this yr, Checkmarx ran a survey asking CISOs about their present AppSec packages. Considered one of our questions particularly requested: “Where are you on your DevSecOps journey?” You may see the solutions beneath:
On the floor, this doesn’t look too dangerous… till you contemplate the small print. Based mostly on our scaling, “medium” solely represents the “definition and strategy” part. The precise means of integration and automation is the place firms really begin “doing” DevSecOps, and just one in 5 firms surveyed have reached that stage in some kind.
And let’s be clear – integration and automation are the objectives of DevSecOps. DevSecOps is about taking the wants and outcomes of software safety and integrating them with the processes and tradition of DevOps. In 10 years, there needs to be no distinction between “DevOps” and “DevSecOps.” DevSecOps is simply what DevOps must be when it grows up.
DevSecOps: The Path to Maturity
OK –how will we get there? If I had been to create a tough sketch of DevSecOps maturity, it will seem like this:
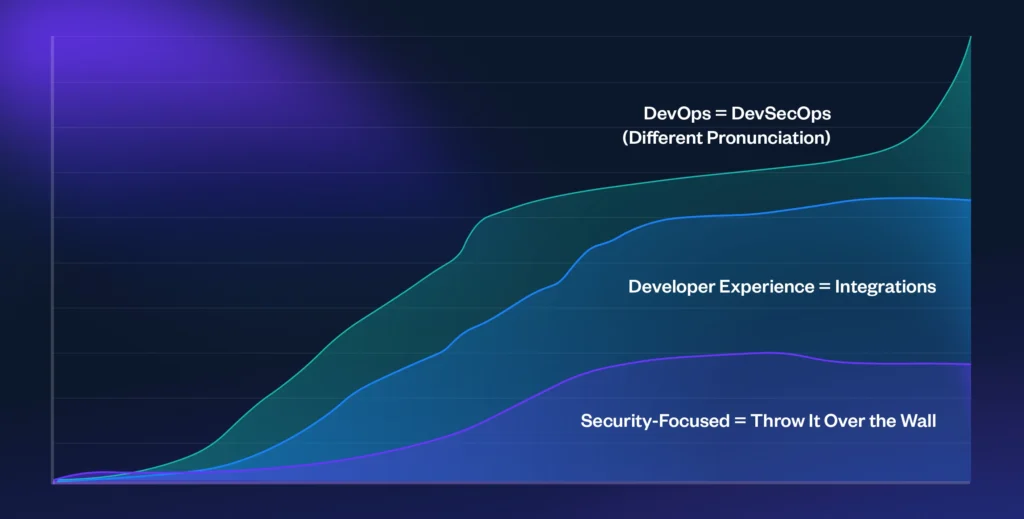
Let’s begin on the underside. That is historically the place AppSec finds vulnerabilities, and basically throws them over the wall to builders and says “here, fix these.” I’ve some dangerous information for you, that is really “Shift Left” in motion. Possibly that’s flippant and a bit unfair; however it’s the base degree of maturity that places organizations on the highway to DevSecOps.
The subsequent degree focuses on the developer expertise. Right here, AppSec groups and builders alike notice that “Shift Left” isn’t actually working. Not as a result of anybody is dangerous, uncaring, or unintelligent, however as a result of it is just meant to be step one. In that stage, AppSec bought instruments to search out and triage vulnerabilities. Now builders want instruments to handle these vulnerabilities themselves with out breaking their workflow. The “developer experience” stage of maturity focuses on IDE-integrations, remediation steering, and different methods to maintain builders centered with out significantly disrupting their circulation.
However like “Shift Left”, specializing in the developer expertise finally hits diminishing returns. Organizations will get caught, after which they might want to start to maneuver in the direction of the third step of maturity. That is the place you are taking the foundational understandings of the primary two steps, and work to outline a DevSecOps tradition.
DevSecOps: Definitely worth the Effort
Tradition is difficult to alter, however fortunately, DevOps individuals have finished it earlier than. If you happen to return to the early days of Agile and Scrum, groups would maintain day by day standups, after which return to working precisely the best way
they’d earlier than. However, as fashionable DevOps organizations can affirm, it’s well worth the effort. For DevSecOps, it’s additionally well worth the effort. Right here is an instance of a Checkmarx buyer’s journey, and you may see them undergo the phases and the outcomes:

It is a chart exhibiting the variety of vulnerabilities remediated by a Fortune 100 firm, and it’s a strong illustration of what issues seem like when groups combine.
If you happen to’re curious concerning the varieties of issues this buyer did to get from the left to proper aspect of the graph above, right here we’ve bought some examples prepared primarily based on the place you might be from a maturity standpoint:
- Shift Left: If you happen to simply must get one thing in place to begin getting vulnerabilities over to builders, the best means is to combine your AppSec instruments along with your suggestions device (watch out right here, you don’t need to instantly shunt 10,000 JIRA tickets over to the devs, so set some insurance policies round it). Click on right here to see a video exhibiting how straightforward that the combination is to do with Checkmarx.
- Developer Expertise: The simplest strategy to begin enhancing your developer expertise is by integrating with their IDE of alternative. That is additionally easy to do with Checkmarx, and here’s a video exhibiting how: Watch now!
- DevSecOps: We’ll discover the keys to DevSecOps intimately within the subsequent weblog, significantly tradition, automation, and velocity, however we talked about the significance of coverage administration in our first bullet level. Whereas designing coverage is tough – it depends on nice communication between growth groups and safety groups – creating and implementing coverage with Checkmarx is simple. Right here’s a video exhibiting the way it’s finished: Watch now!
This weblog is simply our first in a sequence on DevSecOps. Our subsequent weblog will deal with find out how to change tradition, the necessity for automation, and the true which means of “speed” inside the context of DevSecOps. Within the meantime, the movies I simply listed are just some a couple of of these you’ll be able to take a look at over on YouTube
exhibiting how straightforward it’s for platform engineers and builders to combine and work with Checkmarx One. Test them out!