Probably the most vital pillars of a well-architected framework is safety. Thus, it is very important observe these AWS safety finest practices, organized by service, to stop pointless safety conditions.
- AWS IAM
- (1) IAM insurance policies shouldn’t permit full “*” administrative privileges
- (2) IAM customers shouldn’t have IAM insurance policies connected
- (3) IAM customers’ entry keys must be rotated each 90 days or much less
- (4) IAM root consumer entry key shouldn’t exist
- (5) MFA must be enabled for all IAM customers which have a console password
- (6) {Hardware} MFA must be enabled for the foundation consumer
- (7) Password insurance policies for IAM customers ought to have sturdy configurations
- (8) Unused IAM consumer credentials must be eliminated
- Amazon S3
- (9) S3 Block Public Entry setting must be enabled
- (10) S3 buckets ought to have server-side encryption enabled
- (11) S3 Block Public Entry setting must be enabled on the bucket degree
- AWS CloudTrail
- (12) CloudTrail must be enabled and configured with no less than one multi-Area path
- AWS Config
- (15) AWS Config must be enabled
- Amazon EC2
- AWS DMS
- (20) AWS Database Migration Service replication situations shouldn’t be public
- Amazon EBS
- (21) Amazon EBS snapshots shouldn’t be public, decided by the power to be restorable by anybody
- Amazon OpenSearch Service
- (22) Elasticsearch domains ought to have encryption at relaxation enabled
- Amazon SageMaker
- (23) SageMaker pocket book situations shouldn’t have direct web entry
- AWS Lambda
- (24) Lambda capabilities ought to use supported runtimes
- AWS KMS
- (25) AWS KMS keys shouldn’t be unintentionally deleted
- Amazon GuardDuty
- (26) GuardDuty must be enabled
So, you’ve obtained an issue to resolve and turned to AWS to construct and host your answer. You create your account and now you’re all set as much as brew some espresso and sit down at your workstation to architect, code, construct, and deploy. Besides, you aren’t.
There are numerous issues you will need to arrange in order for you your answer to be operative, safe, dependable, performant, and value efficient. And, first issues first, the perfect time to try this is now – proper from the start, earlier than you begin to design and engineer.
Preliminary AWS setup
By no means, ever, use your root account for on a regular basis use. As an alternative, head to Identification and Entry Administration (IAM) and create an administrator consumer. Shield and lock your root credentials in a safe place (is your password sturdy sufficient?) and, in case your root consumer has keys generated, now’s the perfect time to delete them.
You’ll completely need to activate Multi-Issue Authentication (MFA) too to your root account. You could find yourself with a root consumer with MFA and no entry keys. And also you gained’t use this consumer until strictly mandatory.
Now, about your newly created admin account, activating MFA for it’s a should. It’s really a requirement for each consumer in your account if you wish to have a safety first mindset (and also you really need to), however particularly so for energy customers. You’ll solely use this account for administrative functions.

For day by day use, you have to go to the IAM panel and create customers, teams, and roles which may entry solely the assets to which you explicitly grant permissions.
Now you’ve:
- Root account (with no keys) securely locked right into a secure.
- Admin account for administrative use.
- A number of customers, teams, and roles for day after day use.
All of them ought to have MFA activated and powerful passwords.
You’re nearly able to observe the AWS safety finest practices, however first, a phrase of warning in regards to the AWS shared accountability mannequin.
AWS shared accountability mannequin
Safety and compliance is a shared accountability between AWS and the shopper. AWS operates, manages, and controls the elements from the host working system and virtualization layer, all the way down to the bodily safety of the services by which the service operates. The client assumes accountability and administration of the visitor working system (together with updates and safety patches), different related software software program, in addition to the configuration of the AWS supplied safety group firewall.
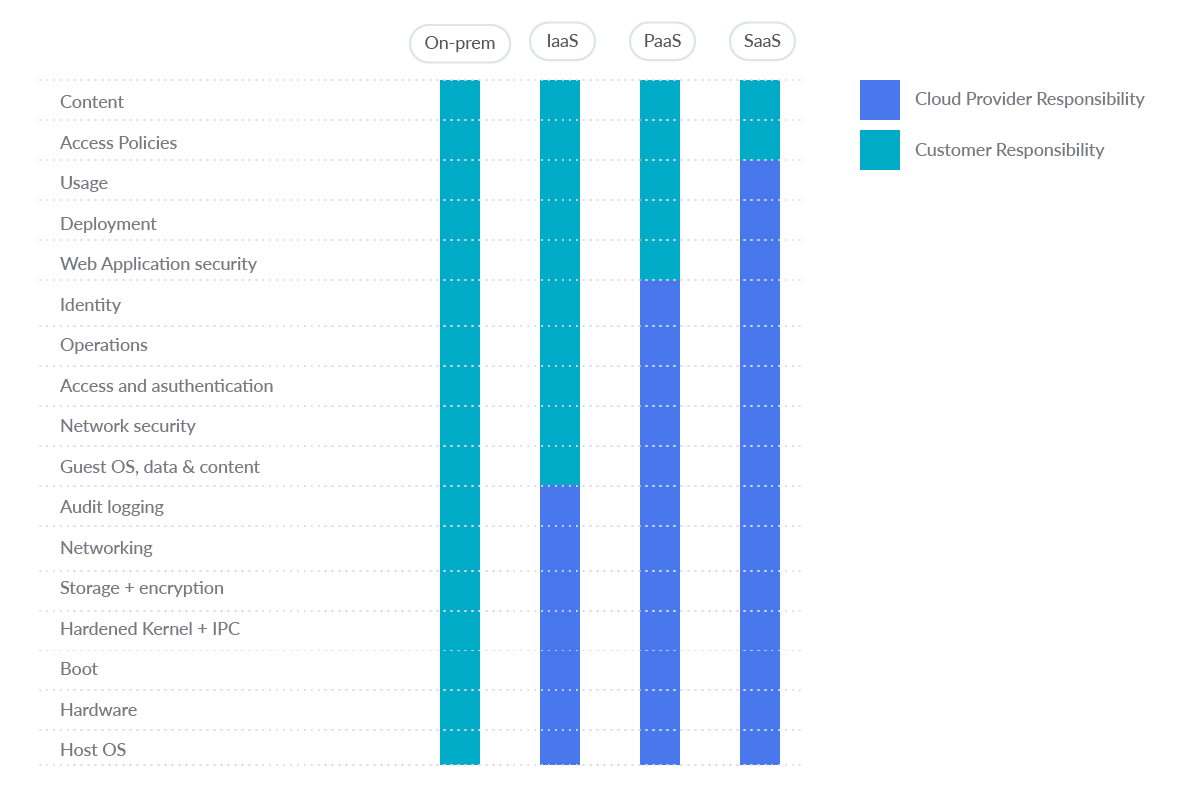
Due to this fact, the administration and software of diligent AWS safety is the accountability of the shopper.
AWS safety finest practices guidelines
On this part we are going to stroll via the commonest AWS providers and supply 26 safety finest practices to undertake.
AWS Safety finest practices with open supply – Cloud Custodian is a Cloud Security Posture Administration (CSPM) device. CSPM instruments consider your cloud configuration and establish frequent configuration errors. In addition they monitor cloud logs to detect threats and configuration modifications.
Now let’s stroll via service by service.
AWS Identification and Entry Administration (IAM)
AWS Identification and Entry Administration (IAM) helps implement least privilege entry management to AWS assets. You need to use IAM to limit who’s authenticated (signed in) and approved (has permissions) to make use of assets.
1.- Don’t permit full “*” administrative privileges on IAM insurance policies 🟥
IAM insurance policies outline a set of privileges which can be granted to customers, teams, or roles. Following commonplace safety recommendation, you must grant least privilege, which suggests to permit solely the permissions which can be required to carry out a job.
Whenever you present full administrative privileges as a substitute of the minimal set of permissions that the consumer wants, you expose the assets to doubtlessly undesirable actions.
For every AWS account, checklist the shopper managed insurance policies obtainable:
aws iam list-policies --scope Native --query 'Insurance policies[*].Arn'Code language: JavaScript (javascript)The earlier command will return a listing of insurance policies together with their Amazon Useful resource Names (ARNs). Utilizing these ARNs, now retrieve the coverage doc in JSON format:
aws iam get-policy-version
--policy-arn POLICY_ARN
--version-id v1
--query 'PolicyVersion.Doc'Code language: JavaScript (javascript)The output must be the requested IAM coverage doc:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "1234567890",
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}Code language: JavaScript (javascript)Look into this doc for the next components:
"Effect": "Allow", "Action": "*", "Resource": "*" Code language: JavaScript (javascript)If these components are current, then the customer-managed coverage permits full administrative privileges. This can be a threat and have to be prevented, so you have to to tune these insurance policies all the way down to pinpoint precisely what actions you need to permit for every particular useful resource.
Repeat the earlier process for the opposite IAM buyer managed insurance policies.
If you wish to detect using full administrative privileges with open supply, here’s a Cloud Custodian rule:
- identify: full-administrative-privileges
description: IAM insurance policies are the means by which privileges are granted to customers, teams, or roles. It's endorsed and thought of a regular safety recommendation to grant least privilege -that is, granting solely the permissions required to carry out a job. Decide what customers must do after which craft insurance policies for them that let the customers carry out solely these duties, as a substitute of permitting full administrative privileges.
useful resource: iam-policy
filters:
- sort: used
- sort: has-allow-allCode language: JavaScript (javascript)2.- Don’t connect IAM insurance policies to customers 🟩
By default, IAM customers, teams, and roles don’t have any entry to AWS assets.
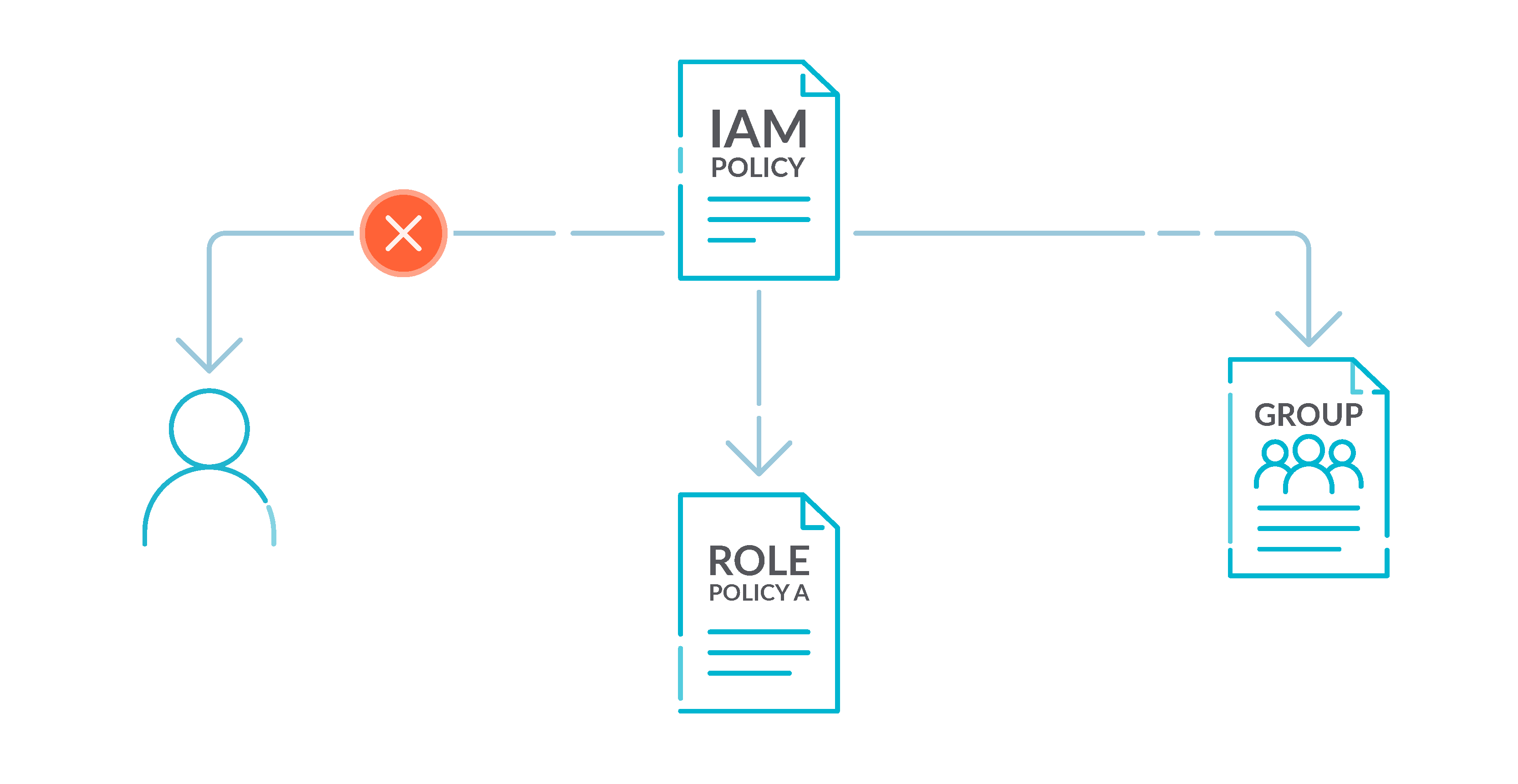
IAM insurance policies grant privileges to customers, teams, or roles. We suggest that you just apply IAM insurance policies on to teams and roles however to not customers. Assigning privileges on the group or position degree reduces the complexity of entry administration because the variety of customers grows. Lowering entry administration complexity would possibly in flip scale back the chance for a principal to inadvertently obtain or retain extreme privileges.
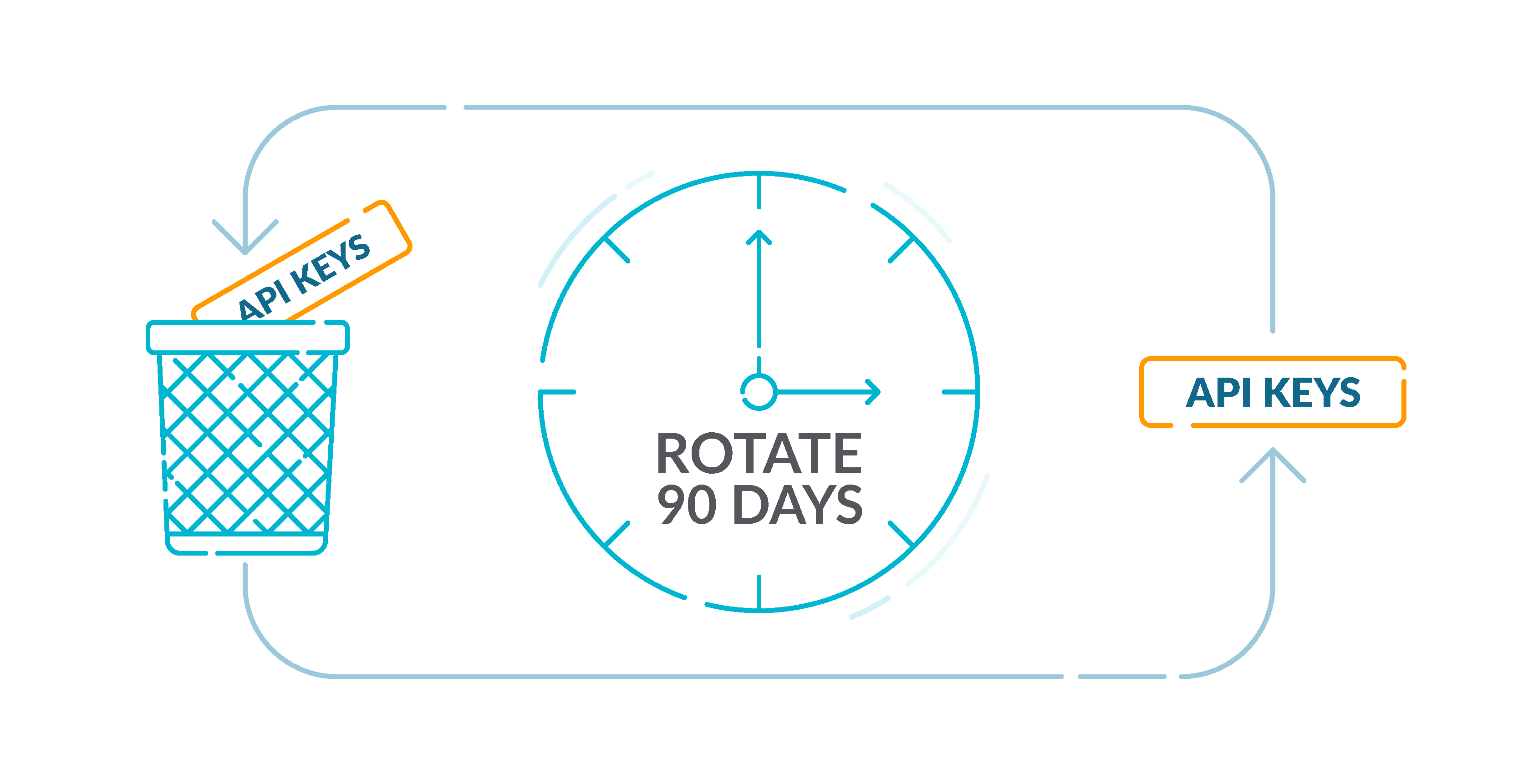
3.- Rotate IAM customers’ entry keys each 90 days or much less 🟨
AWS recommends that you just rotate the entry keys each 90 days. Rotating entry keys reduces the possibility that an entry key that’s related to a compromised or terminated account is used. It additionally ensures that knowledge can’t be accessed with an outdated key which may have been misplaced, cracked, or stolen. At all times replace your purposes after you rotate entry keys.
First, checklist all IAM customers obtainable in your AWS account with:
aws iam list-users --query 'Customers[*].UserName'Code language: JavaScript (javascript)For all of the customers returned by this command, decide every lively entry key lifetime by doing:
aws iam list-access-keys --user-name USER_NAMECode language: JavaScript (javascript)This could expose the metadata for every entry key current for the required IAM consumer. The output will appear to be this:
{
"AccessKeyMetadata": [
{
"UserName": "some-user",
"Status": "Inactive",
"CreateDate": "2022-05-18T13:43:23Z",
"AccessKeyId": "AAAABBBBCCCCDDDDEEEE"
},
{
"UserName": "some-user",
"Status": "Active",
"CreateDate": "2022-03-21T09:12:32Z",
"AccessKeyId": "AAAABBBBCCCCDDDDEEEE"
}
]
}Code language: JavaScript (javascript)Test the CreateDate parameter worth for every lively key to find out its creation time. If an lively entry key has been created earlier than the final 90 days, the bottom line is outdated and have to be rotated to safe the entry to your AWS assets.
Repeat for every IAM consumer current in your AWS account.
4.- Make sure that IAM root consumer entry keys don’t exist 🟥
As we acknowledged throughout your preliminary setup, we extremely suggest that you just take away all entry keys which can be related to the foundation consumer. This limits the vectors that can be utilized to compromise your account. It additionally encourages the creation and use of role-based accounts which can be least privileged.
The next Cloud Custodian rule will verify if root entry keys have been used in your account:
- identify: root-access-keys
description: The basis consumer account is essentially the most privileged consumer in an AWS account. AWS Entry Keys present programmatic entry to a given AWS account. It's endorsed that each one entry keys related with the foundation consumer account be eliminated.
useful resource: account
filters:
- sort: iam-summary
key: AccountAccessKeysPresent
worth: 0
op: gtCode language: JavaScript (javascript)5.- Allow MFA for all IAM customers which have a console password 🟨
Multi-factor authentication (MFA) provides an additional layer of safety on prime of a username and password. With MFA enabled, when a consumer indicators in to an AWS web site, they’re prompted for his or her username and password. As well as, they’re prompted for an authentication code from their AWS MFA gadget.
We suggest that you just allow MFA for all accounts which have a console password. MFA is designed to offer elevated safety for console entry. The authenticating principal should possess a tool that emits a time-sensitive key and will need to have information of a credential.
Should you nonetheless need to add one other layer of safety, we suggest monitoring your logins with MFA to detect spam, let’s proceed with extra AWS safety finest practices.
6.- Allow {hardware} MFA for the foundation consumer 🟥
Digital MFA may not present the identical degree of safety as {hardware} MFA gadgets. A {hardware} MFA has a minimal assault floor, and can’t be stolen until the malicious consumer features bodily entry to the {hardware} gadget. We suggest that you just use solely a digital MFA gadget when you anticipate {hardware} buy approval or to your {hardware} to reach, particularly for root customers.
To study extra, see Enabling a digital multi-factor authentication (MFA) gadget (console) within the IAM Consumer Information.
Here’s a Cloud Custodian rule to detect lack of root {hardware} MFA:
- identify: root-hardware-mfa
description: The basis consumer account is essentially the most privileged consumer in an AWS account. MFA provides an additional layer of safety on prime of a username and password. With MFA enabled, when a consumer indicators in to an AWS web site, they are going to be prompted for their username and password as properly as for an authentication code from their AWS MFA gadget. It's endorsed that the foundation consumer account be protected with a {hardware} MFA.
useful resource: account
filters:
- or:
- sort: iam-summary
key: AccountMFAEnabled
worth: 1
op: ne
- and:
- sort: iam-summary
key: AccountMFAEnabled
worth: 1
op: eq
- sort: has-virtual-mfa
worth: trueCode language: JavaScript (javascript)7.- Guarantee these password insurance policies for IAM customers have sturdy configurations 🟨
We suggest that you just implement the creation of sturdy consumer passwords. You’ll be able to set a password coverage in your AWS account to specify complexity necessities and necessary rotation durations for passwords.
Whenever you create or change a password coverage, many of the password coverage settings are enforced the following time customers change their passwords. A number of the settings are enforced instantly.
What constitutes a powerful password is a subjective matter, however the next settings will put you on the suitable path:
RequireUppercaseCharacters: true
RequireLowercaseCharacters: true
RequireSymbols: true
RequireNumbers: true
MinimumPasswordLength: 8Code language: JavaScript (javascript)8.- Take away unused IAM consumer credentials 🟨
IAM customers can entry AWS assets utilizing various kinds of credentials, similar to passwords or entry keys. We suggest you take away or deactivate all credentials that have been unused for 90 days or extra to cut back the window of alternative for credentials related to a compromised or deserted account for use.
You need to use the IAM console to get among the info that you have to monitor accounts for dated credentials. For instance, while you view customers in your account, there’s a column for Entry key age, Password age, and Final exercise. If the worth in any of those columns is bigger than 90 days, make the credentials for these customers inactive.
You may as well use credential studies to watch consumer accounts and establish these with no exercise for 90 or extra days. You’ll be able to obtain credential studies in .csv format from the IAM console.
For extra info, try AWS safety finest practices for IAM in additional element.

Amazon S3
Amazon Easy Storage Service (Amazon S3) is an object storage service providing industry-leading scalability, knowledge availability, safety, and efficiency. There are few AWS safety finest practices to undertake on the subject of S3.
9.- Allow S3 Block Public Entry setting 🟨
Amazon S3 public entry block is designed to offer controls throughout a whole AWS account or on the particular person S3 bucket degree to make sure that objects by no means have public entry. Public entry is granted to buckets and objects via entry management lists (ACLs), bucket insurance policies, or each.

Until you plan to have your S3 buckets be publicly accessible, you must configure the account degree Amazon S3 Block Public Entry characteristic.
Get the names of all S3 buckets obtainable in your AWS account:
aws s3api list-buckets --query 'Buckets[*].Title'Code language: JavaScript (javascript)For every bucket returned, get its S3 Block Public Entry characteristic configuration:
aws s3api get-public-access-block --bucket BUCKET_NAMECode language: JavaScript (javascript)The output for the earlier command must be like this:
"PublicAccessBlockConfiguration": {
"BlockPublicAcls": false,
"IgnorePublicAcls": false,
"BlockPublicPolicy": false,
"RestrictPublicBuckets": false
}Code language: JavaScript (javascript)If any of those values is fake, then your knowledge privateness is at stake. Use this brief command to remediate it:
aws s3api put-public-access-block
--region REGION
--bucket BUCKET_NAME
--public-access-block-configuration BlockPublicAcls=true,IgnorePublicAcls=true,BlockPublicPolicy=true,RestrictPublicBuckets=true Code language: JavaScript (javascript)10.- Allow server-side encryption on S3 buckets 🟥
For an added layer of safety to your delicate knowledge in S3 buckets, you must configure your buckets with server-side encryption to guard your knowledge at relaxation.
Amazon S3 encrypts every object with a novel key. As a further safeguard, Amazon S3 encrypts the important thing itself with a root key that it rotates often. Amazon S3 server-side encryption makes use of one of many strongest block ciphers obtainable to encrypt your knowledge, 256-bit Superior Encryption Commonplace (AES-256).
Checklist all current S3 buckets obtainable in your AWS account:
aws s3api list-buckets --query 'Buckets[*].Title'Code language: Perl (perl)Now, use the names of the S3 buckets returned on the earlier step as identifiers to retrieve their Default Encryption characteristic standing:
aws s3api get-bucket-encryption --bucket BUCKET_NAMECode language: Perl (perl)The command output ought to return the requested characteristic configuration particulars. If the get-bucket-encryption command output returns an error message, the default encryption isn’t presently enabled, and due to this fact the chosen S3 bucket doesn’t routinely encrypt all objects when saved in Amazon S3.
Repeat this process for all of your S3 buckets.
11.- Allow S3 Block Public Entry setting on the bucket degree 🟨
Amazon S3 public entry block is designed to offer controls throughout a whole AWS account or on the particular person S3 bucket degree to make sure that objects by no means have public entry. Public entry is granted to buckets and objects via entry management lists (ACLs), bucket insurance policies, or each.
Until you plan to have your S3 buckets be publicly accessible, which you most likely shouldn’t, you must configure the account degree Amazon S3 Block Public Entry characteristic.
You need to use this Cloud Custodian rule to detect S3 buckets which can be publicly accessible:
- identify: buckets-public-access-block
description: Amazon S3 offers Block public entry (bucket settings) and Block public entry (account settings) that can assist you handle public entry to Amazon S3 assets. By default, S3 buckets and objects are created with public entry disabled. Nevertheless, an IAM precept with enough S3 permissions can allow public entry on the bucket and/or object degree. Whereas enabled, Block public entry (bucket settings) prevents a person bucket, and its contained objects, from changing into publicly accessible. Equally, Block public entry (account settings) prevents all buckets, and contained objects, from changing into publicly accessible throughout the whole account.
useful resource: s3
filters:
- or:
- sort: check-public-block
BlockPublicAcls: false
- sort: check-public-block
BlockPublicPolicy: false
- sort: check-public-block
IgnorePublicAcls: false
- sort: check-public-block
RestrictPublicBuckets: falseCode language: Perl (perl)AWS CloudTrail
After IAM, inside the AWS safety finest practices, CloudTrail is crucial service to contemplate when detecting threats.
AWS CloudTrail is an AWS service that helps you allow governance, compliance, and operational and threat auditing of your AWS account. Actions taken by a consumer, position, or AWS service are recorded as occasions in CloudTrail.
Occasions embody actions taken within the AWS Administration Console, AWS Command Line Interface, and AWS SDKs and APIs. Uncover the variations between CloudTrail vs CloudWatch
The next part will allow you to configure CloudTrail to watch your infrastructure throughout all of your areas.
12.- Allow and configure CloudTrail with no less than one multi-Area path 🟥
CloudTrail offers a historical past of AWS API requires an account, together with API calls created from the AWS Administration Console, AWS SDKs, and command line instruments. The historical past additionally contains API calls from higher-level AWS providers, similar to AWS CloudFormation.
The AWS API name historical past produced by CloudTrail permits safety evaluation, useful resource change monitoring, and compliance auditing. Multi-Area trails additionally present the next advantages.
- A multi-Area path helps to detect sudden exercise occurring in in any other case unused Areas.
- A multi-Area path ensures that international service occasion logging is enabled for a path by default. International service occasion logging data occasions generated by AWS international providers.
- For a multi-Area path, administration occasions for all learn and write operations be sure that CloudTrail data administration operations on all of an AWS account’s assets.
By default, CloudTrail trails which can be created utilizing the AWS Administration Console are multi-Area trails.
Checklist all trails obtainable within the chosen AWS area:
aws cloudtrail describe-trailsCode language: Perl (perl)The output exposes every AWS CloudTrail path together with its configuration particulars. If IsMultiRegionTrail config parameter worth is fake, the chosen path isn’t presently enabled for all AWS areas:
{
"trailList": [
{
"IncludeGlobalServiceEvents": true,
"Name": "ExampleTrail",
"TrailARN": "arn:aws:cloudtrail:us-east-1:123456789012:trail/ExampleTrail",
"LogFileValidationEnabled": false,
"IsMultiRegionTrail": false,
"S3BucketName": "ExampleLogging",
"HomeRegion": "us-east-1"
}
]
}Code language: Perl (perl)Confirm that your entire trails and ensure no less than one is multi-Area.
13.- Allow encryption at relaxation with CloudTrail 🟨
Test whether or not CloudTrail is configured to make use of the server-side encryption (SSE) AWS Key Administration Service buyer grasp key (CMK) encryption.
The verify passes if the KmsKeyId is outlined. For an added layer of safety to your delicate CloudTrail log recordsdata, you must use server-side encryption with AWS KMS–managed keys (SSE-KMS) to your CloudTrail log recordsdata for encryption at relaxation. Observe that by default, the log recordsdata delivered by CloudTrail to your buckets are encrypted by Amazon server-side encryption with Amazon S3-managed encryption keys (SSE-S3).
You’ll be able to verify that the logs are encrypted with the next Cloud Custodian rule:
- identify: cloudtrail-logs-encrypted-at-rest
description: AWS CloudTrail is an online service that data AWS API calls for an account and makes these logs obtainable to customers and assets in accordance with IAM insurance policies. AWS Key Administration Service (KMS) is a managed service that helps create and management the encryption keys used to encrypt account knowledge, and makes use of {Hardware} Safety Modules (HSMs) to guard the safety of encryption keys. CloudTrail logs may be configured to leverage server facet encryption (SSE) and KMS buyer created grasp keys (CMK) to additional shield CloudTrail logs. It's endorsed that CloudTrail be configured to use SSE-KMS.
useful resource: cloudtrail
filters:
- sort: worth
key: KmsKeyId
worth: absentCode language: Perl (perl)You’ll be able to remediate it utilizing the AWS Console like this:
- Register to the AWS Administration Console at https://console.aws.amazon.com/cloudtrail/.
- Within the left navigation panel, choose Trails.
- Beneath the Title column, choose the path identify that you have to replace.
- Click on the pencil icon subsequent to the S3 part to edit the path bucket configuration.
- Beneath S3 bucket* click on Superior.
- Choose Sure subsequent to Encrypt log recordsdata to encrypt your log recordsdata with SSE-KMS utilizing a Buyer Grasp Key (CMK).
- Choose Sure subsequent to Create a brand new KMS key to create a brand new CMK and enter a reputation for it, or in any other case choose No to make use of an current CMK encryption key obtainable within the area.
- Click on Save to allow SSE-KMS encryption.
14.- Allow CloudTrail log file validation 🟨
CloudTrail log file validation creates a digitally signed digest file that accommodates a hash of every log that CloudTrail writes to Amazon S3. You need to use these digest recordsdata to find out whether or not a log file was modified, deleted, or unchanged after CloudTrail delivered the log.
It’s endorsed that you just allow file validation on all trails. Log file validation offers further integrity checks of CloudTrail logs.
To verify this within the AWS Console proceed as follows:
- Register to the AWS Administration Console at https://console.aws.amazon.com/cloudtrail/.
- Within the left navigation panel, choose Trails.
- Beneath the Title column, choose the path identify that you have to study.
- Beneath S3 part, verify for Allow log file validation standing:
- Allow log file validation standing. If the characteristic standing is ready to No, then the chosen path doesn’t have log file integrity validation enabled. If that is so, repair it:
- Click on the pencil icon subsequent to the S3 part to edit the path bucket configuration.
- Beneath S3 bucket* click on Superior and seek for the Allow log file validation configuration standing.
- Choose Sure to allow log file validation, after which click on Save.
Study extra about safety finest practices in AWS Cloudtrail.
AWS Config
AWS Config offers an in depth view of the assets related together with your AWS account, together with how they’re configured, how they’re associated to at least one one other, and the way the configurations and their relationships have modified over time.
15.- Confirm AWS Config is enabled 🟥
The AWS Config service performs configuration administration of supported AWS assets in your account and delivers log recordsdata to you. The recorded info contains the configuration merchandise (AWS useful resource), relationships between configuration gadgets, and any configuration modifications between assets.
It’s endorsed that you just allow AWS Config in all Areas. The AWS configuration merchandise historical past that AWS Config captures permits safety evaluation, useful resource change monitoring, and compliance auditing.
Get the standing of all configuration recorders and supply channels created by the Config service within the chosen area:
aws configservice --region REGION get-statusCode language: Perl (perl)The output from the earlier command reveals the standing of all AWS Config supply channels and configuration recorders obtainable. If AWS Config isn’t enabled, the checklist for each configuration recorders and supply channels are proven empty:
Configuration Recorders:
Supply Channels:Code language: Perl (perl)Or, if the service was beforehand enabled however is now disabled, the standing must be set to OFF:
Configuration Recorders:
identify: default
recorder: OFF
Supply Channels:
identify: default
final stream supply standing: NOT_APPLICABLE
final historical past supply standing: SUCCESS
final snapshot supply standing: SUCCESSCode language: Perl (perl)To remediate this, after you allow AWS Config, configure it to file all assets.
- Open the AWS Config console at https://console.aws.amazon.com/config/.
- Choose the Area to configure AWS Config in.
- Should you haven’t used AWS Config earlier than, see Getting Began within the AWS Config Developer Information.
- Navigate to the Settings web page from the menu, and do the next:
- Select Edit.
- Beneath Useful resource varieties to file, choose File all assets supported on this area and Embody international assets (e.g., AWS IAM assets).
- Beneath Knowledge retention interval, select the default retention interval for AWS Config knowledge, or specify a customized retention interval.
- Beneath AWS Config position, both select Create AWS Config service-linked position or select Select a job out of your account after which choose the position to make use of.
- Beneath Amazon S3 bucket, specify the bucket to make use of or create a bucket and optionally embody a prefix.
- Beneath Amazon SNS subject, choose an Amazon SNS subject out of your account or create one. For extra details about Amazon SNS, see the Amazon Easy Notification Service Getting Began Information.
- Select Save.
To go deeper, observe the AWS safety finest practices for AWS Config.
Amazon EC2
Amazon Elastic Compute Cloud (Amazon EC2) is an online service that gives resizable computing capability that you just use to construct and host your software program programs. Due to this fact, EC2 is among the core providers of AWS and it’s essential to know the perfect safety practices and the way to safe EC2.
16.- Guarantee connected EBS volumes are encrypted at relaxation 🟥
It’s to verify whether or not the EBS volumes which can be in an connected state are encrypted. To go this verify, EBS volumes have to be in use and encrypted. If the EBS quantity isn’t connected, then it’s not topic to this verify.
For an added layer of safety to your delicate knowledge in EBS volumes, you must allow EBS encryption at relaxation. Amazon EBS encryption provides an easy encryption answer to your EBS assets that doesn’t require you to construct, preserve, and safe your personal key administration infrastructure. It makes use of KMS keys when creating encrypted volumes and snapshots.
Run the describe-volumes command to find out in case your EC2 Elastic Block Retailer quantity is encrypted:
aws ec2 describe-volumes
--filters Title=attachment.instance-id, Values=INSTANCE_IDCode language: Perl (perl)The command output ought to reveal the occasion EBS quantity encryption standing (true for enabled, false for disabled).
There isn’t any direct solution to encrypt an current unencrypted quantity or snapshot. You’ll be able to solely encrypt a brand new quantity or snapshot while you create it.
Should you allow encryption by default, Amazon EBS encrypts the ensuing new quantity or snapshot through the use of your default key for Amazon EBS encryption. Even when you have not enabled encryption by default, you may allow encryption while you create a person quantity or snapshot. In each instances, you may override the default key for Amazon EBS encryption and select a symmetric buyer managed key.
17.- Allow VPC circulation logging in all VPCs 🟩
With the VPC Movement Logs characteristic, you may seize details about the IP handle site visitors going to and from community interfaces in your VPC. After you create a circulation log, you may view and retrieve its knowledge in CloudWatch Logs. To cut back value, you can even ship your circulation logs to Amazon S3.
It’s endorsed that you just allow circulation logging for packet rejects for VPCs. Movement logs present visibility into community site visitors that traverses the VPC and might detect anomalous site visitors or present perception throughout safety workflows. By default, the file contains values for the totally different elements of the IP handle circulation, together with the supply, vacation spot, and protocol.
- identify: flow-logs-enabled
description: VPC Movement Logs is a characteristic that lets you seize details about the IP site visitors going to and from community interfaces in your VPC. After you've created a circulation log, you may view and retrieve its knowledge in Amazon CloudWatch Logs. It's endorsed that VPC Movement Logs be enabled for packet 'Rejects' for VPCs.
useful resource: vpc
filters:
- not:
- sort: flow-logs
enabled: trueCode language: Perl (perl)18.- Verify the VPC default safety group doesn’t permit inbound and outbound site visitors 🟩
The foundations for the default safety group permit all outbound and inbound site visitors from community interfaces (and their related situations) which can be assigned to the identical safety group.
We don’t suggest utilizing the default safety group. As a result of the default safety group can’t be deleted, you must change the default safety group guidelines setting to limit inbound and outbound site visitors. This prevents unintended site visitors if the default safety group is by chance configured for assets, similar to EC2 situations.
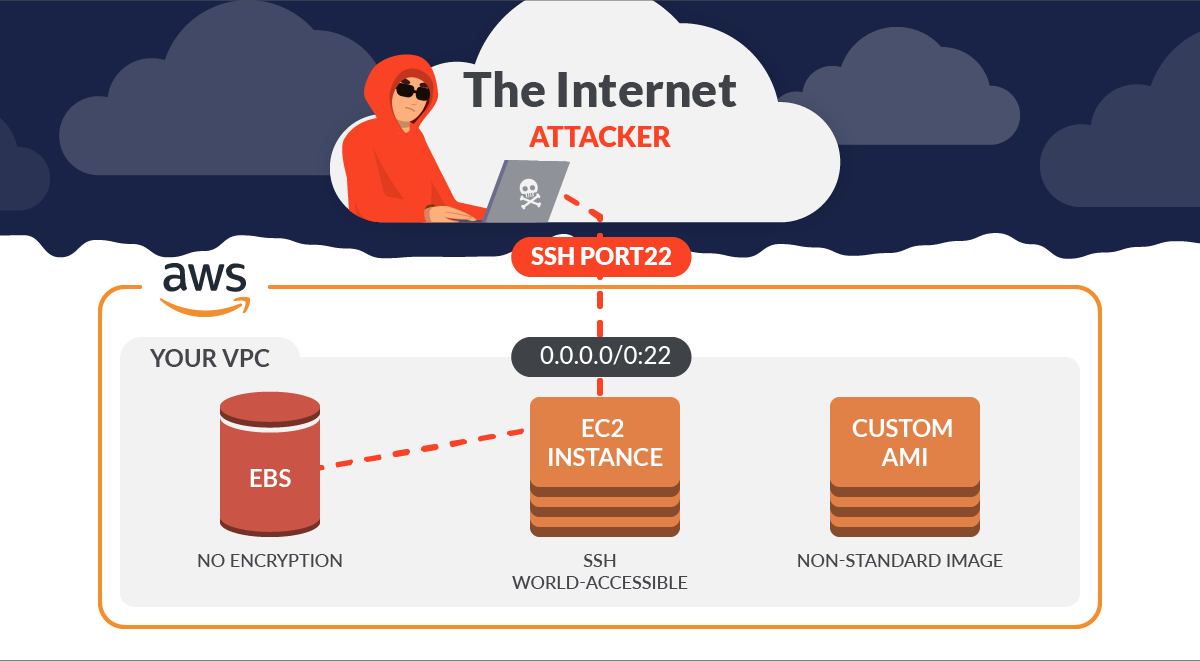
Get the outline of the default safety group inside the chosen area:
aws ec2 describe-security-groups
--region REGION
--filters Title=group-name,Values='default'
--output desk
--query 'SecurityGroups[*].IpPermissions[*].IpRanges'Code language: Perl (perl)If this command doesn’t return any output, then the default safety group doesn’t permit public inbound site visitors. In any other case, it ought to return the inbound site visitors supply IPs outlined, as within the following instance:
------------------------
|DescribeSecurityGroups|
+----------------------+
| CidrIp |
+----------------------+
| 0.0.0.0/0 |
| ::/0 |
| 1.2.3.4/32 |
| 1.2.3.5/32 |
+----------------------+Code language: Perl (perl)If the IPs returned are 0.0.0.0/0 or ::/0, then the chosen default safety group is permitting public inbound site visitors. We’ve defined beforehand what the actual threats are when securing SSH on EC2.
To remediate this subject, create new safety teams and assign these safety teams to your assets. To forestall the default safety teams from getting used, take away their inbound and outbound guidelines.
19.- Allow EBS default encryption 🟥
When encryption is enabled to your account, Amazon EBS volumes and snapshot copies are encrypted at relaxation. This provides a further layer of safety to your knowledge. For extra info, see Encryption by default within the Amazon EC2 Consumer Information for Linux Situations.
Observe that following occasion varieties don’t assist encryption: R1, C1, and M1.
Run the get-ebs-encryption-by-default command to know whether or not EBS encryption by default is enabled to your AWS cloud account within the chosen area:
aws ec2 get-ebs-encryption-by-default
--region REGION
--query 'EbsEncryptionByDefault'Code language: Perl (perl)If the command returns false, the encryption of knowledge at relaxation by default for brand spanking new EBS volumes isn’t enabled within the chosen AWS area. Repair it with the next command:
aws ec2 enable-ebs-encryption-by-default
--region REGIONCode language: Perl (perl)AWS Database Migration Service (DMS)
AWS Database Migration Service (AWS DMS) is a cloud service that makes it simple emigrate relational databases, knowledge warehouses, NoSQL databases, and different sorts of knowledge shops. You need to use AWS DMS emigrate your knowledge into the AWS Cloud or between mixtures of cloud and on-premises setups.
20.- Confirm AWS Database Migration Service replication situations should not public 🟥
Make sure that your Amazon Database Migration Service (DMS) isn’t publicly accessible from the Web to be able to keep away from exposing personal knowledge and decrease safety dangers. A DMS replication occasion ought to have a non-public IP handle and the Publicly Accessible characteristic disabled when each the supply and the goal databases are in the identical community that’s linked to the occasion’s VPC via a VPN, VPC peering connection, or utilizing an AWS Direct Join devoted connection.
- Register to AWS Administration Console at https://console.aws.amazon.com/dms/.
- Within the left navigation panel, select Replication situations.
- Choose the DMS replication occasion that you just need to study to open the panel with the useful resource configuration particulars.
- Choose the Overview tab from the dashboard backside panel and verify the Publicly accessible configuration attribute worth. If the attribute worth is ready to Sure, the chosen Amazon DMS replication occasion is accessible outdoors the Digital Personal Cloud (VPC) and may be uncovered to safety dangers. To repair it, do the next:
- Click on the Create replication occasion button from the dashboard prime menu to provoke the launch course of.
- On Create replication occasion web page, carry out the next:
- Uncheck Publicly accessible checkbox to disable the general public entry to the brand new replication occasion. If this setting is disabled, Amazon DMS won’t assign a public IP handle to the occasion at creation and also you won’t be able to connect with the supply/goal databases outdoors the VPC.
- Present a novel identify for the brand new replication occasion inside the Title field, then configure the remainder of the occasion settings utilizing the configuration info copied at step No. 5.
- Click on Create replication occasion to launch your new Amazon DMS occasion.
- Replace your database migration plan by creating a brand new migration job to incorporate the newly created AWS DMS replication occasion.
- To cease including fees for the outdated replication occasion:
- Choose the outdated DMS occasion, then click on the Delete button from the dashboard prime menu.
- Throughout the Delete replication occasion dialog field, overview the occasion particulars then click on Delete to terminate the chosen DMS useful resource.
- Repeat step Nos. 3 and 4 for every AWS DMS replication occasion provisioned within the chosen area.
- Change the area from the console navigation bar and repeat the method for all the opposite areas.
Study extra about AWS safety finest practices for AWS Database Migration Service.

Amazon Elastic Block Retailer (EBS)
Amazon Elastic Block Retailer (Amazon EBS) offers block degree storage volumes to be used with EC2 situations. EBS volumes behave like uncooked, unformatted block gadgets. You’ll be able to mount these volumes as gadgets in your situations. EBS volumes which can be connected to an occasion are uncovered as storage volumes that persist independently from the lifetime of the occasion. You’ll be able to create a file system on prime of those volumes, or use them in any method you’ll use a block gadget (similar to a tough drive).
You’ll be able to dynamically change the configuration of a quantity connected to an occasion.
21.- Guarantee Amazon EBS snapshots should not public, or to be restored by anybody 🟥
EBS snapshots are used to again up the information in your EBS volumes to Amazon S3 at a selected time limit. You need to use the snapshots to revive earlier states of EBS volumes. It’s not often acceptable to share a snapshot with the general public. Sometimes, the choice to share a snapshot publicly was made in error or with out a full understanding of the implications. This verify helps be sure that all such sharing was absolutely deliberate and intentional.
Get the checklist of all EBS quantity snapshots:
aws ec2 describe-snapshots
--region REGION
--owner-ids ACCOUNT_ID
--filters Title=standing,Values=accomplished
--output desk
--query 'Snapshots[*].SnapshotId'Code language: Perl (perl)For every snapshot, verify its createVolumePermission attribute:
aws ec2 describe-snapshot-attribute
--region REGION
--snapshot-id SNAPSHOT_ID
--attribute createVolumePermission
--query 'CreateVolumePermissions[]'Code language: Perl (perl)The output from the earlier command returns details about the permissions for creating EBS volumes from the chosen snapshot:
{
"Group": "all"
}Code language: Perl (perl)If the command output is "Group": "all", the snapshot is accessible to all AWS accounts and customers. If that is so, take your time to run this command to repair it:
aws ec2 modify-snapshot-attribute
--region REGION
--snapshot-id SNAPSHOT_ID
--attribute createVolumePermission
--operation-type take away
--group-names allCode language: Perl (perl)Amazon OpenSearch Service
Amazon OpenSearch Service is a managed service that makes it simple to deploy, function, and scale OpenSearch clusters within the AWS Cloud. Amazon OpenSearch Service is the successor to Amazon Elasticsearch Service and helps OpenSearch and legacy Elasticsearch OSS (as much as 7.10, the ultimate open supply model of the software program). Whenever you create a cluster, you’ve the choice of which search engine to make use of.
22.- Guarantee Elasticsearch domains have encryption at relaxation enabled 🟥
For an added layer of safety to your delicate knowledge in OpenSearch, you must configure your OpenSearch to be encrypted at relaxation. Elasticsearch domains provide encryption of knowledge at relaxation. The characteristic makes use of AWS KMS to retailer and handle your encryption keys. To carry out the encryption, it makes use of the Superior Encryption Commonplace algorithm with 256-bit keys (AES-256).
Checklist all Amazon OpenSearch domains presently obtainable:
aws es list-domain-names --region REGIONCode language: Perl (perl)Now decide if data-at-rest encryption characteristic is enabled with:
aws es describe-elasticsearch-domain
--region REGION
--domain-name DOMAIN_NAME
--query 'DomainStatus.EncryptionAtRestOptions'Code language: Perl (perl)If the Enabled flag is fake, the data-at-rest encryption isn’t enabled for the chosen Amazon ElasticSearch area. Repair it with:
aws es create-elasticsearch-domain
--region REGION
--domain-name DOMAIN_NAME
--elasticsearch-version 5.5
--elasticsearch-cluster-config InstanceType=m4.massive.elasticsearch,InstanceCount=2
--ebs-options EBSEnabled=true,VolumeType=commonplace,VolumeSize=200
--access-policies file://supply-domain-access-policy.json
--vpc-options SubnetIds=SUBNET_ID,SecurityGroupIds=SECURITY_GROUP_ID
--encryption-at-rest-options Enabled=true,KmsKeyId=KMS_KEY_IDCode language: Perl (perl)As soon as the brand new cluster is provisioned, add the present knowledge (exported from the unique cluster) to the newly created cluster.
In spite of everything the information is uploaded, it’s secure to take away the unencrypted OpenSearch area to cease incurring fees for the useful resource:
aws es delete-elasticsearch-domain
--region REGION
--domain-name DOMAIN_NAMECode language: Perl (perl)Amazon SageMaker
Amazon SageMaker is a fully-managed machine studying service. With Amazon SageMaker, knowledge scientists and builders can shortly construct and practice machine studying fashions, after which deploy them right into a production-ready hosted setting.
23.- Confirm SageMaker pocket book situations don’t have direct web entry 🟨
Should you configure your SageMaker occasion with out a VPC, then, by default, direct web entry is enabled in your occasion. It’s best to configure your occasion with a VPC and alter the default setting to Disable — Entry the web via a VPC.
To coach or host fashions from a pocket book, you want web entry. To allow web entry, make it possible for your VPC has a NAT gateway and your safety group permits outbound connections. To study extra about the way to join a pocket book occasion to assets in a VPC, see “Connect a notebook instance to resources in a VPC” within the Amazon SageMaker Developer Information.
You also needs to be sure that entry to your SageMaker configuration is restricted to solely approved customers. Prohibit customers’ IAM permissions to switch SageMaker settings and assets.
- Register to the AWS Administration Console at https://console.aws.amazon.com/sagemaker/.
- Within the navigation panel, beneath Pocket book, select Pocket book situations.
- Choose the SageMaker pocket book occasion that you just need to study and click on on the occasion identify (hyperlink).
- On the chosen occasion configuration web page, inside the Community part, verify for any VPC subnet IDs and safety group IDs. If these community configuration particulars should not obtainable, as a substitute the next standing is displayed: “No custom VPC settings applied.” The pocket book occasion isn’t working inside a VPC community, due to this fact you may observe the steps described on this conformity rule to deploy the occasion inside a VPC. In any other case, if the pocket book occasion is working inside a VPC, verify the Direct web entry configuration attribute worth. If the attribute worth is ready to Enabled, the chosen Amazon SageMaker pocket book occasion is publicly accessible.
If the pocket book has direct web entry enabled, repair it by recreating it with this CLI command:
aws sagemaker create-notebook-instance
--region REGION
--notebook-instance-name NOTEBOOK_INSTANCE_NAME
--instance-type INSTANCE_TYPE
--role-arn ROLE_ARN
--kms-key-id KMS_KEY_ID
--subnet-id SUBNET_ID
--security-group-ids SECURITY_GROUP_ID
--direct-internet-access DisabledCode language: Perl (perl)AWS Lambda
With AWS Lambda, you may run code with out provisioning or managing servers. You pay just for the compute time that you just devour — there’s no cost when your code isn’t working. You’ll be able to run code for just about any sort of software or backend service — all with zero administration.
Simply add your code and Lambda takes care of all the things required to run and scale your code with excessive availability. You’ll be able to arrange your code to routinely set off from different AWS providers or name it instantly from any internet or cellular app.
You will need to point out the issues that might happen if we don’t safe or audit the code we execute in our lambda capabilities, as you would be the preliminary entry for attackers.
24.- Use supported runtimes for Lambda capabilities 🟨
This AWS safety finest observe recommends checking that the Lambda perform settings for runtimes match the anticipated values set for the supported runtimes for every language. This management checks perform settings for the next runtimes: nodejs16.x, nodejs14.x, nodejs12.x, python3.9, python3.8, python3.7, ruby2.7, java11, java8, java8.al2, go1.x, dotnetcore3.1, and dotnet6.
The AWS Config rule ignores capabilities which have a package deal sort of picture.
Lambda runtimes are constructed round a mix of working system, programming language, and software program libraries which can be topic to upkeep and safety updates. When a runtime part is not supported for safety updates, Lambda deprecates the runtime. Although you can’t create capabilities that use the deprecated runtime, the perform continues to be obtainable to course of invocation occasions. Make it possible for your Lambda capabilities are present and don’t use out-of-date runtime environments.
Get the names of all Amazon Lambda capabilities obtainable within the chosen AWS cloud area:
aws lambda list-functions
--region REGION
--output desk
--query 'Features[*].FunctionName'Code language: Perl (perl)Now study the runtime info obtainable for every capabilities:
aws lambda get-function-configuration
--region REGION
--function-name FUNCTION_NAME
--query 'Runtime'Code language: Perl (perl)Examine the worth returned with the up to date checklist of Amazon Lambda runtimes supported by AWS, in addition to the tip of assist plan listed within the AWS documentation.
If the runtime is unsupported, repair it to make use of the newest runtime model. For instance:
aws lambda update-function-configuration
--region REGION
--function-name FUNCTION_NAME
--runtime "nodejs16.x"Code language: Perl (perl)AWS Key Administration Service (AWS KMS)
AWS Key Administration Service (AWS KMS) is an encryption and key administration service scaled for the cloud. AWS KMS keys and performance are utilized by different AWS providers, and you need to use them to guard knowledge in your personal purposes that use AWS.
25.- Don’t unintentionally delete AWS KMS keys 🟨
KMS keys can’t be recovered as soon as deleted. Knowledge encrypted beneath a KMS key can be completely unrecoverable if the KMS secret is deleted. If significant knowledge has been encrypted beneath a KMS key scheduled for deletion, take into account decrypting the information or re-encrypting the information beneath a brand new KMS key until you’re deliberately performing a cryptographic erasure.
When a KMS secret is scheduled for deletion, a compulsory ready interval is enforced to permit time to reverse the deletion if it was scheduled in error. The default ready interval is 30 days, however it may be decreased to as brief as seven days when the KMS secret is scheduled for deletion. Through the ready interval, the scheduled deletion may be canceled and the KMS key won’t be deleted.
Checklist all Buyer Grasp keys obtainable within the chosen AWS area:
aws kms list-keys --region REGIONCode language: Perl (perl)Run the describe-key command for every CMK to establish any keys scheduled for deletion:
aws kms describe-key --key-id KEY_IDCode language: Perl (perl)The output for this command reveals the chosen key metadata. If the KeyState worth is ready to PendingDeletion, the bottom line is scheduled for deletion. But when this isn’t what you really need (the commonest case), unschedule the deletion with:
aws kms cancel-key-deletion --key-id KEY_IDCode language: Perl (perl)Amazon GuardDuty
Amazon GuardDuty is a steady safety monitoring service. Amazon GuardDuty will help to establish sudden and doubtlessly unauthorized or malicious exercise in your AWS setting.
26.- Allow GuardDuty 🟨
It’s extremely really helpful that you just allow GuardDuty in all supported AWS Areas. Doing so permits GuardDuty to generate findings about unauthorized or uncommon exercise, even in Areas that you don’t actively use. This additionally permits GuardDuty to watch CloudTrail occasions for international AWS providers, similar to IAM.
Checklist the IDs of all the present Amazon GuardDuty detectors. A detector is an object that represents the AWS GuardDuty service. A detector have to be created to ensure that GuardDuty to turn into operational:
aws guardduty list-detectors
--region REGION
--query 'DetectorIds'Code language: Perl (perl)If the list-detectors command output returns an empty array, then there are not any GuardDuty detectors obtainable. On this occasion, the Amazon GuardDuty service isn’t enabled inside your AWS account. If that is so, create a detector with the next command:
aws guardduty create-detector
--region REGION
--enableCode language: Perl (perl)As soon as the detector is enabled, it’ll begin to pull and analyze impartial streams of knowledge from AWS CloudTrail, VPC circulation logs, and DNS logs to be able to generate findings.
AWS compliance requirements & benchmarks
Establishing and sustaining your AWS infrastructure to maintain it safe is a endless effort that may require numerous time.
For this, you can be higher off following the compliance commonplace(s) related to your {industry}, since they supply all the necessities wanted to successfully safe your cloud setting.
Due to the continuing nature of securing your setting and complying with a safety commonplace, you may also need to recurrently run insurance policies, similar to CIS Amazon Internet Providers Foundations Benchmark, which can audit your system and report any non-conformity it finds based mostly on AWS safety finest practices.
Conclusion
Going all cloud opens a brand new world of prospects, however it additionally opens a large door to attacking vectors. Every new AWS service you leverage has its personal set of potential risks you want to concentrate on and properly ready for.
Fortunately, cloud native safety instruments like Falco and Cloud Custodian can information you thru these finest practices, and allow you to meet your compliance necessities, in addition to make sure you observe AWS safety finest practices.

If you wish to know the way to configure and handle all these providers, Sysdig will help you enhance your Cloud Security Posture Administration (CSPM). Dig deeper with the next assets:
Register for our Free 30-day trial and see for your self!