COMMENTARY
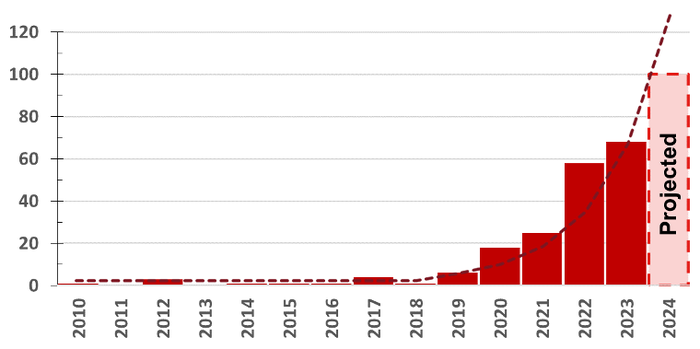
Waterfall Safety Options, in collaboration with ICS Try, not too long ago launched its “2024 Menace Report.” The unhealthy information is that, in 2023, there have been 68 cyberattacks that took down greater than 500 bodily operations. The excellent news (type of) is that that is solely 19% extra assaults than the earlier yr. What is going on on? Ransomware assaults with bodily penalties are down barely, hacktivist assaults are fixed, and all the pieces else is rising. The report’s authors conclude that the 19% enhance is most probably an aberration, and that we’ll see a rise nearer to 90% to 100% in 2024.
The Particulars
Waterfall’s operational expertise (OT) safety risk report is probably the most cautious within the business — it tracks solely deliberate cyberattacks that brought about bodily penalties in constructing automation, heavy business, manufacturing, and important industrial infrastructures within the public document. That’s, no non-public or confidential disclosures. The entire information set for the report is included in its appendix. This implies the report is for certain to be an underestimate of what is actually occurring on the earth, as a result of the authors report common confidential disclosures that they can’t embody of their counts.
OT incidents since 2010. Supply: “2024 Threat Report,” Waterfall Safety Options, in collaboration with ICS Try
Extra Assaults
Regardless of this underestimate, cyberattacks that met the inclusion standards proceed to extend, practically doubling yearly since 2019. This can be a massive change from 2010–2019, when OT assaults with bodily penalties had been flat, bouncing round between zero and 5 assaults yearly.
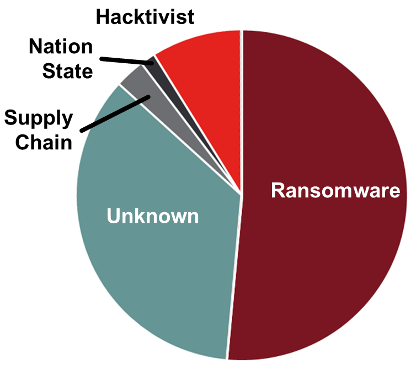
Menace actors. Supply: “2024 Threat Report,” Waterfall Safety Options, in collaboration with ICS Try
What are these assaults? In 24 of 68 circumstances, there was not sufficient info within the public document to attribute the assault. Of the remaining, 35 assaults (80%) had been ransomware, six (14%) had been hacktivists, two had been provide chain assaults, and one was attributed to a nation state. The 35 ransomware assaults are down barely from final yr’s 41, which is sudden, provided that ransomware assaults on IT networks proceed to extend at between 60% to 70% per yr, relying on the report. Why? Partially, as a result of public stories this yr had been much less detailed, there have been many extra “unknown” risk actors this yr.
One other issue has to do with the truth that most ransomware assaults that affect bodily operations did so solely unintentionally — both due to “abundance of caution” OT shutdowns, when IT is impaired, or bodily operations being depending on crippled IT infrastructure. In 2023, we noticed a cloth fraction of ransomware felony teams shift away from encrypting and disabling techniques to easily stealing the info and demanding ransoms to destroy the stolen information slightly than publish it. With fewer IT techniques being crippled via encryption, it appears to be like like fewer OT techniques and bodily operations are being impaired.
We count on this pattern to stabilize in 2024, and for OT impacts because of ransomware return to the not too long ago historic norm of practically doubling yearly. Why? As a result of not all companies have information they’re keen to pay to guard. Such companies, particularly crucial infrastructures, should still, nonetheless, pay a ransom to revive performance to crippled techniques, so it is smart that at the very least some ransomware criminals won’t depart cash on the desk and can proceed to cripple servers, along with stealing what information they will.
Provide Chain
Provide chain assaults with bodily penalties confirmed up this yr for the primary time in a few years. Newag SA was accused of embedding code in its trains to maximise the revenues of approved restore retailers. It’s accused of performing to “lock up the practice with bogus error codes after some date, or if the practice wasn’t operating for a time frame.” A few of the code was discovered to include GPS coordinates to restrict the habits to third-party workshops. Newag denies the accusations, blaming “unknown hackers.” And in an obvious contractual dispute, ORQA, a producer of first-person view (FPV) digital actuality headsets, had its merchandise locked up by what it describes as a “greedy former contractor.”
Wrapping Up
There are a lot of different findings within the report: GPS blocking and spoofing is changing into a widespread drawback, manufacturing companies accounted for a couple of half of the assaults with outages, hacktivists are focusing on crucial infrastructures, and there may be an alarming batch of close to misses, together with the various crucial infrastructures and utilities focused by China’s Volt Storm “living off the land” marketing campaign. The report additionally touches on promising new developments on the defensive facet, together with the Cyber-Knowledgeable Engineering Technique.